サイトコンテンツ
関連ニュース
最終更新日: 2026-03-04 06:00
-
「Chrome」の「Gemini」に深刻度「高」の脆弱性--速やかにパッチ適用を - ZDNET Japan
2026-03-03 21:50 japan.zdnet.com -
LinkedInの公開データが30分で標的型攻撃に転用されるリスク:AIが標的分析を高速化
2026-03-03 21:11 www.trendmicro.com -
3月3日(火)日本経済新聞主催の「SECURITY SHOW 2026」に 関通・代表取締役の達城久裕が登壇
2026-03-02 11:02 ecnomikata.com -
「Langflow」にプロンプトインジェクションによるRCE脆弱性 - Security NEXT
2026-03-02 02:32 www.security-next.com -
Claude Codeに重大な脆弱性 設定ファイル経由でRCEやAPIキー窃取の恐れ - ITmedia
2026-02-28 10:24 www.itmedia.co.jp -
攻撃者のAI利用はもはや“当たり前” 日本はランサムウェア検出率で世界3位に - ITmedia
2026-02-28 09:50 www.itmedia.co.jp -
Gmailアカウントのセキュリティを今すぐ確認せよ、攻撃が進行中だ - Yahoo!ニュース
2026-02-28 06:25 news.yahoo.co.jp -
中国によるChatGPTを使った高市早苗首相への信用失墜攻撃を拒否したとOpenAIが公表
2026-02-28 03:05 gigazine.net -
自律型AIからの攻撃対策 | 企業をむしばむリスクとその対策
2026-02-27 18:08 www.risktaisaku.com -
Box Japanが「情報セキュリティ10大脅威 2026」を解説、「ランサム攻撃はBoxで回避できる」と ...
2026-02-27 14:45 cloud.watch.impress.co.jp -
ネットワンパートナーズ、米Xage Securityと販売代理店契約を締結 ゼロトラストセキュリティー ...
2026-02-27 13:31 www.weeklybcn.com -
AI主導時代の幕開け Ciscoが警告する2026年の脅威動向と防御戦略の転換 - ITmedia
2026-02-27 10:50 www.itmedia.co.jp -
統合防御を実現するデータレイヤーセキュリティのVAST Data、CrowdStrikeと ... - AT PARTNERS
2026-02-27 09:33 www.atpartners.co.jp -
エルテス、マルチモーダルAIを活用しSNS上の画像情報を解析する「画像リスク検知サービス」
2026-02-26 19:36 cloud.watch.impress.co.jp -
ラック、セキュリティ専門家が発刊する「LAC Security Insight 第15号 2026 冬」を公開
2026-02-26 12:34 www.dreamnews.jp -
イスラエル発のAIネイティブなサイバーセキュリティスタートアップの"Gambit Security"がSeedと ...
2026-02-26 05:53 www.atpartners.co.jp -
Anthropic、コード分析により複雑な脆弱性も発見できる新機能「Claude Code Security」提供開始
2026-02-24 15:51 www.itmedia.co.jp -
「攻撃はAI、 対応は人間」ではもう守り切れない。サイバーセキュリティ対策の“改変”を徹底生解説
2026-02-24 14:14 prtimes.jp -
Anthropic、コード分析により複雑な脆弱性も発見できる新機能「Claude Code Security」提供開始
2026-02-24 13:31 www.itmedia.co.jp -
Anthropicが自律的AI脆弱性検出ツール「Claude Code Security」をリリース - ビジネス+IT
2026-02-23 17:17 www.sbbit.jp
※ この情報は、当ウェブサイトが設定したキーワードにもとづきGoogle Alertsの機能を利用して収集されたものです。これらの情報は第三者のウェブサイトやコンテンツから取得されており、その内容について当ウェブサイトは関与しておりません。
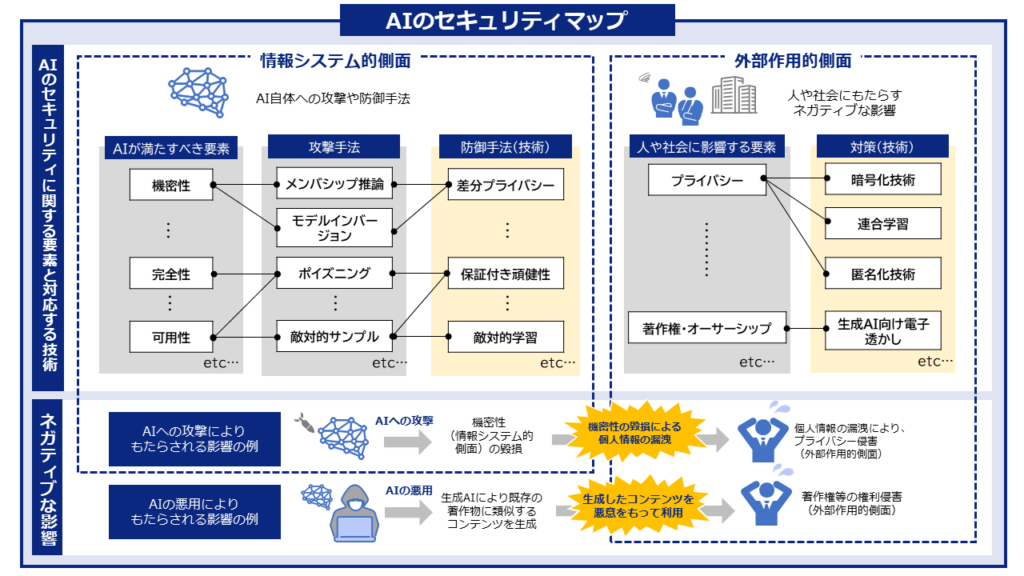
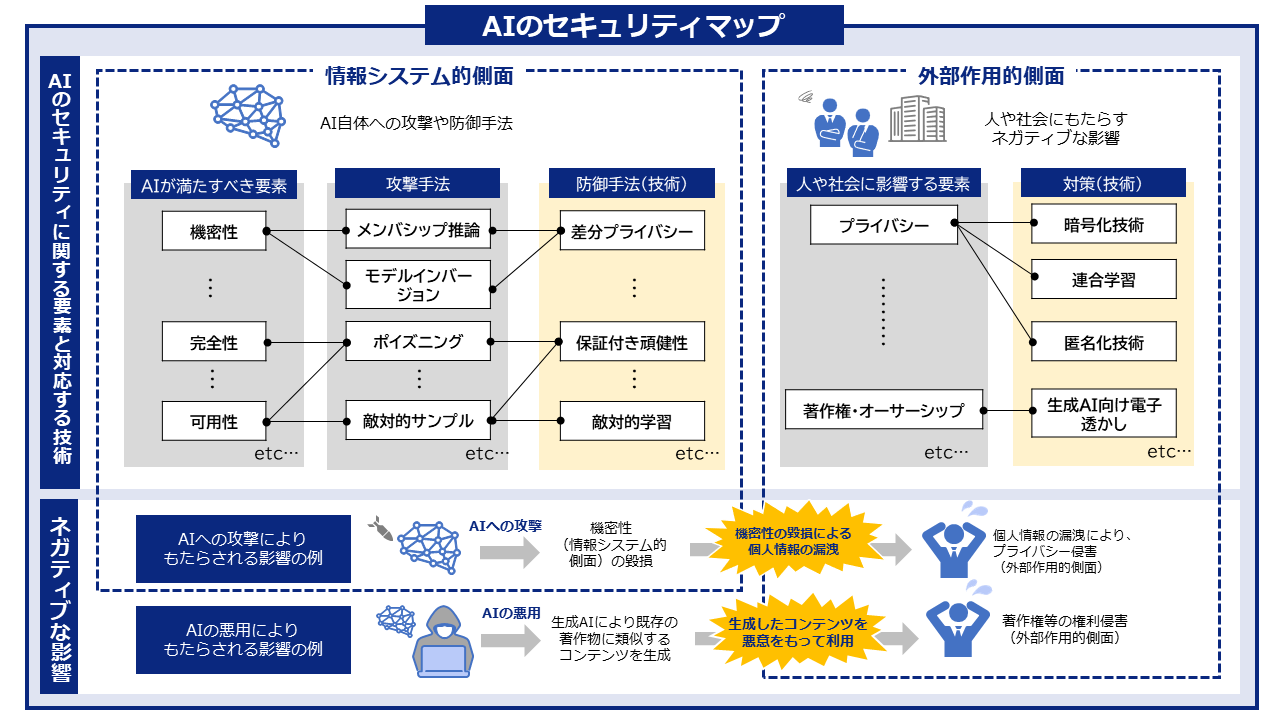
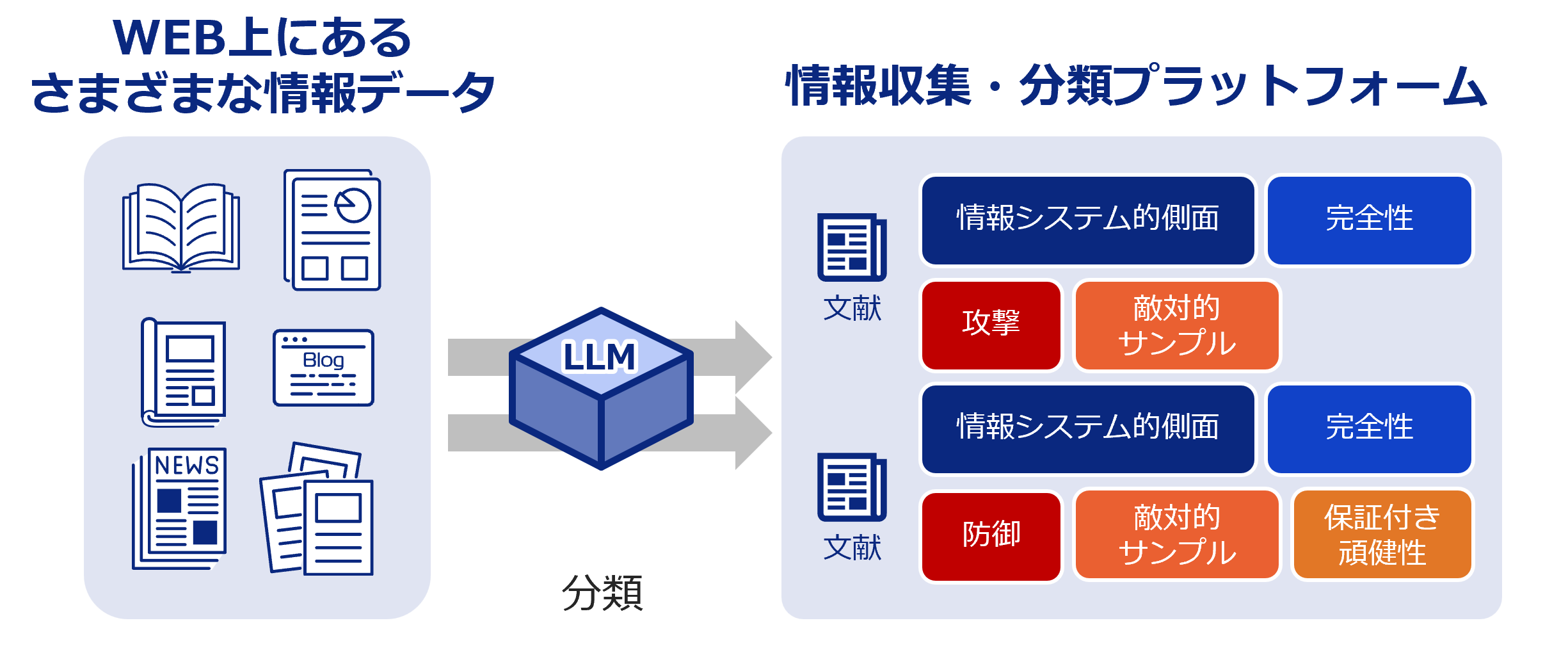
新着文献

Protection against Source Inference Attacks in Federated Learning
Authors: Andreas Athanasiou, Kangsoo Jung, Catuscia Palamidessi | Published: 2026-03-02
2026.03.02

Real Money, Fake Models: Deceptive Model Claims in Shadow APIs
Authors: Yage Zhang, Yukun Jiang, Zeyuan Chen, Michael Backes, Xinyue Shen, Yang Zhang | Published: 2026-03-02
2026.03.02

Co-Evolutionary Multi-Modal Alignment via Structured Adversarial Evolution
Authors: Guoxin Shi, Haoyu Wang, Zaihui Yang, Yuxing Wang, Yongzhe Chang | Published: 2026-03-02
2026.03.02

-scaled.png)