サイトコンテンツ
関連ニュース
最終更新日: 2026-02-06 06:04
-
アドイン経由で「Outlook」から機密メールを盗む「Exfil Out&Look」攻撃 - Yahoo!ニュース
2026-02-06 01:40 news.yahoo.co.jp -
バルテス、オンラインカンファレンス「Security MOTION 2026 Spring」に登壇 - PR TIMES
2026-02-06 00:48 prtimes.jp -
エムオーテックス主催カンファレンス「Security MOTION 2026 Spring」に登壇 | 株式会社エルテス
2026-02-06 00:04 digitalpr.jp -
エムオーテックス主催カンファレンス「Security MOTION 2026 Spring」に登壇 - 紀伊民報
2026-02-05 18:51 www.agara.co.jp -
アドイン経由で「Outlook」から機密メールを盗む「Exfil Out&Look」攻撃 - 窓の杜
2026-02-05 18:03 forest.watch.impress.co.jp -
AIセキュリティのCoWorker、「脆弱性診断サービス」提供開始--自社開発AI「Red Agent」×専門家 ...
2026-02-04 11:37 www.jiji.com -
「ServiceNow」に深刻な脆弱性 - 2025年10月更新で修正済み - Security NEXT
2026-02-04 09:07 www.security-next.com -
GMO Flatt Security、鈴木もも香が執行役員CHROに就任 - ASCII.jp
2026-02-04 08:57 ascii.jp -
プレスリリース:GMO Flatt Security、鈴木もも香が執行役員CHROに就任(PR TIMES) | 毎日新聞
2026-02-04 08:50 mainichi.jp -
AIが脆弱性を探し、ランサムウェア構築を支援 5つのAI悪用手口と対策リスト:ESET解説 - @IT
2026-02-03 14:37 atmarkit.itmedia.co.jp -
AIセキュリティのCoWorker、「脆弱性診断サービス」提供開始——自社開発AI「Red Agent ...
2026-02-03 13:04 prtimes.jp -
「Aisuru」ボットネット、史上最大規模のDDoS攻撃を実施 - ZDNET Japan
2026-02-03 12:35 japan.zdnet.com -
SentinelOne、完全自律型プラットフォームで実現するAI時代の高度な防御 - ZDNET Japan
2026-02-03 05:45 japan.zdnet.com -
AIがサイバー攻撃の実行役になった2025年 攻防の実情をGoogleセキュリティCTOに聞いた …
2026-02-02 13:41 news.yahoo.co.jp -
サイバー攻撃対策ソフトおすすめ比較10選!料金やメリット・選び方ポイント - BOXIL SaaS
2026-02-02 11:08 boxil.jp -
「AI Security asilla」がVer4.2へアップデート - STRAIGHT PRESS[ストレートプレス]
2026-01-31 10:14 straightpress.jp -
身代金ウイルス、攻撃常態化AIリスクへの対策重要/NTTデータ - ガスエネルギー新聞
2026-01-30 23:52 www.gas-enenews.co.jp -
ゼットスケーラー、生成AI時代に対応するセキュリティサービス「Zscaler AI Security Suite」を発表
2026-01-30 11:02 news.mynavi.jp -
ゼットスケーラー、生成AI時代に対応するセキュリティサービス「Zscaler AI Security Suite」を発表
2026-01-30 09:01 topics.smt.docomo.ne.jp -
ゼットスケーラー、ゼロトラスト基盤でAI活用を保護する「AI Security Suite」提供開始
2026-01-29 14:56 businessnetwork.jp
※ この情報は、当ウェブサイトが設定したキーワードにもとづきGoogle Alertsの機能を利用して収集されたものです。これらの情報は第三者のウェブサイトやコンテンツから取得されており、その内容について当ウェブサイトは関与しておりません。
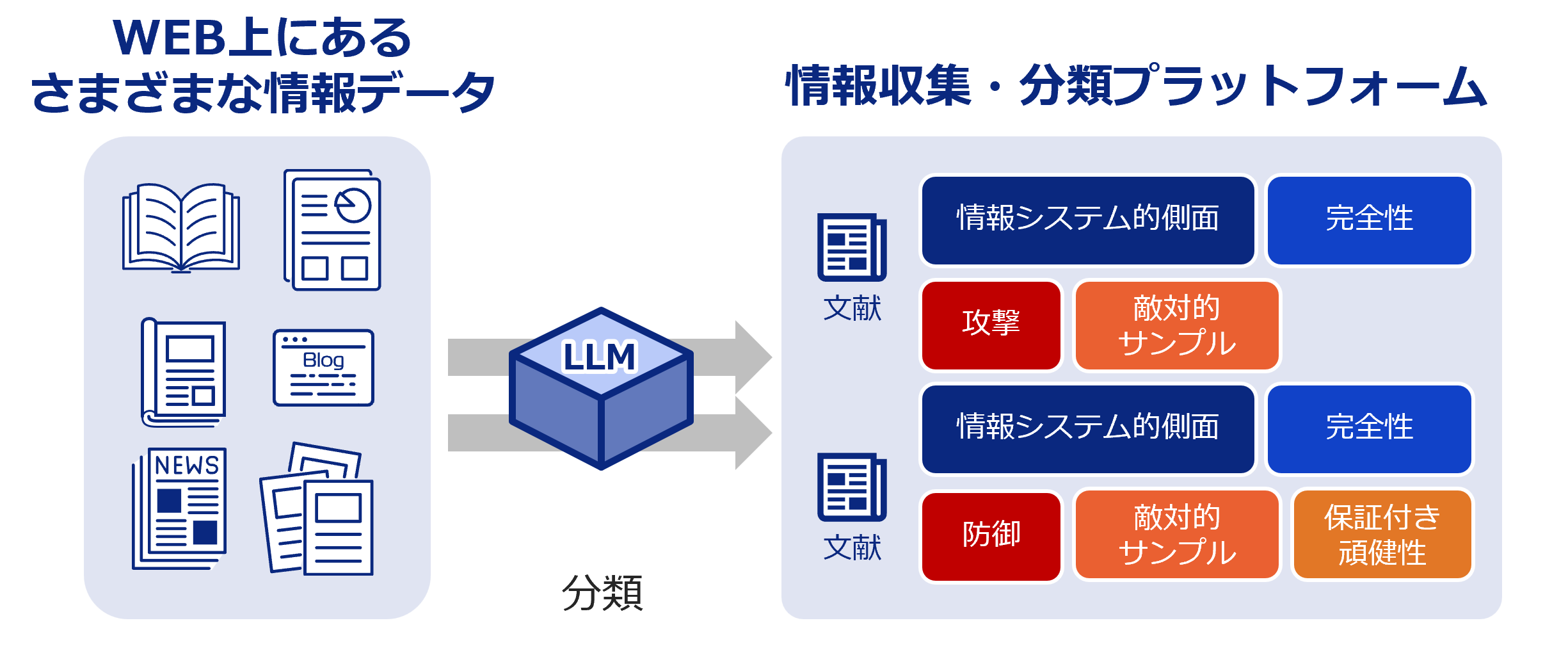
新着文献

Comparative Insights on Adversarial Machine Learning from Industry and Academia: A User-Study Approach
Authors: Vishruti Kakkad, Paul Chung, Hanan Hibshi, Maverick Woo | Published: 2026-02-04
2026.02.04

How Few-shot Demonstrations Affect Prompt-based Defenses Against LLM Jailbreak Attacks
Authors: Yanshu Wang, Shuaishuai Yang, Jingjing He, Tong Yang | Published: 2026-02-04
2026.02.04

Semantic Consensus Decoding: Backdoor Defense for Verilog Code Generation
Authors: Guang Yang, Xing Hu, Xiang Chen, Xin Xia | Published: 2026-02-04
2026.02.04

-scaled.png)