サイトコンテンツ
関連ニュース
最終更新日: 2026-02-04 06:01
-
AIが脆弱性を探し、ランサムウェア構築を支援 5つのAI悪用手口と対策リスト:ESET解説 - @IT
2026-02-03 23:37 atmarkit.itmedia.co.jp -
AIセキュリティのCoWorker、「脆弱性診断サービス」提供開始——自社開発AI「Red Agent ...
2026-02-03 22:04 prtimes.jp -
「Aisuru」ボットネット、史上最大規模のDDoS攻撃を実施 - ZDNET Japan
2026-02-03 21:35 japan.zdnet.com -
SentinelOne、完全自律型プラットフォームで実現するAI時代の高度な防御 - ZDNET Japan
2026-02-03 14:45 japan.zdnet.com -
AIがサイバー攻撃の実行役になった2025年 攻防の実情をGoogleセキュリティCTOに聞いた …
2026-02-02 13:41 news.yahoo.co.jp -
サイバー攻撃対策ソフトおすすめ比較10選!料金やメリット・選び方ポイント - BOXIL SaaS
2026-02-02 11:08 boxil.jp -
「AI Security asilla」がVer4.2へアップデート - STRAIGHT PRESS[ストレートプレス]
2026-01-31 10:14 straightpress.jp -
身代金ウイルス、攻撃常態化AIリスクへの対策重要/NTTデータ - ガスエネルギー新聞
2026-01-30 23:52 www.gas-enenews.co.jp -
ゼットスケーラー、生成AI時代に対応するセキュリティサービス「Zscaler AI Security Suite」を発表
2026-01-30 11:02 news.mynavi.jp -
ゼットスケーラー、生成AI時代に対応するセキュリティサービス「Zscaler AI Security Suite」を発表
2026-01-30 09:01 topics.smt.docomo.ne.jp -
ゼットスケーラー、ゼロトラスト基盤でAI活用を保護する「AI Security Suite」提供開始
2026-01-29 14:56 businessnetwork.jp -
2026年のサイバー攻撃はランサムウェアとAI詐欺が焦点、動向を踏まえた対策見直しが課題である
2026-01-29 14:18 act1.co.jp -
「pwn2own automotive 2026」に当社エンジニアの古川 和祈が出場しました | 脆弱性診断 ...
2026-01-29 08:54 gmo-cybersecurity.com -
「セキュリティ10大脅威2026」発表 - 多岐にわたる脅威「AIリスク」が初選出 - Security NEXT
2026-01-29 08:29 www.security-next.com -
「Security MOTION 2026 Spring」にて講演します | 株式会社NTTデータ先端技術
2026-01-28 15:48 www.intellilink.co.jp -
ランサムウェア対策を含む企業のサイバー防御を強化する、マイクロセグメンテーション ...
2026-01-28 12:32 prtimes.jp -
ランサムウェアが猛威を振るう、AI詐欺に注意…2026年「サイバー攻撃」で脅威となるのは何か ...
2026-01-28 06:05 news.yahoo.co.jp -
HPE OneViewの重大な脆弱性に対する活発な悪用を警告 組織は直ちにパッチ適用を
2026-01-26 06:30 www.fnn.jp -
AIエコノミー時代のセキュリティ予測 - 2026年は防御側が主導権を握る年
2026-01-26 04:30 news.mynavi.jp -
「Active Directory」狙う6つの攻撃、「Chrome拡張」のマルウェア化 知らぬ間に広がるリスク - IT
2026-01-24 09:14 atmarkit.itmedia.co.jp
※ この情報は、当ウェブサイトが設定したキーワードにもとづきGoogle Alertsの機能を利用して収集されたものです。これらの情報は第三者のウェブサイトやコンテンツから取得されており、その内容について当ウェブサイトは関与しておりません。
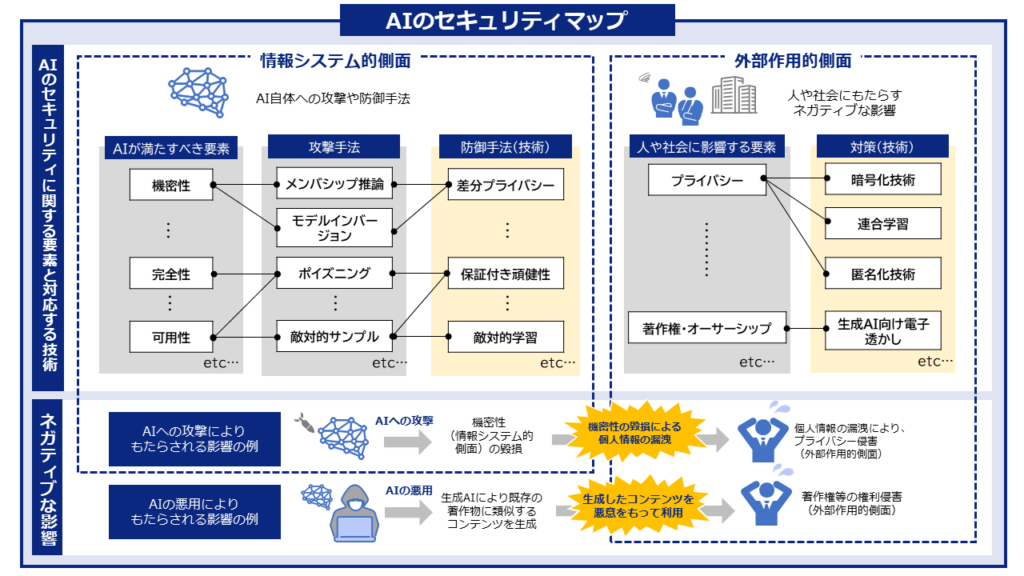
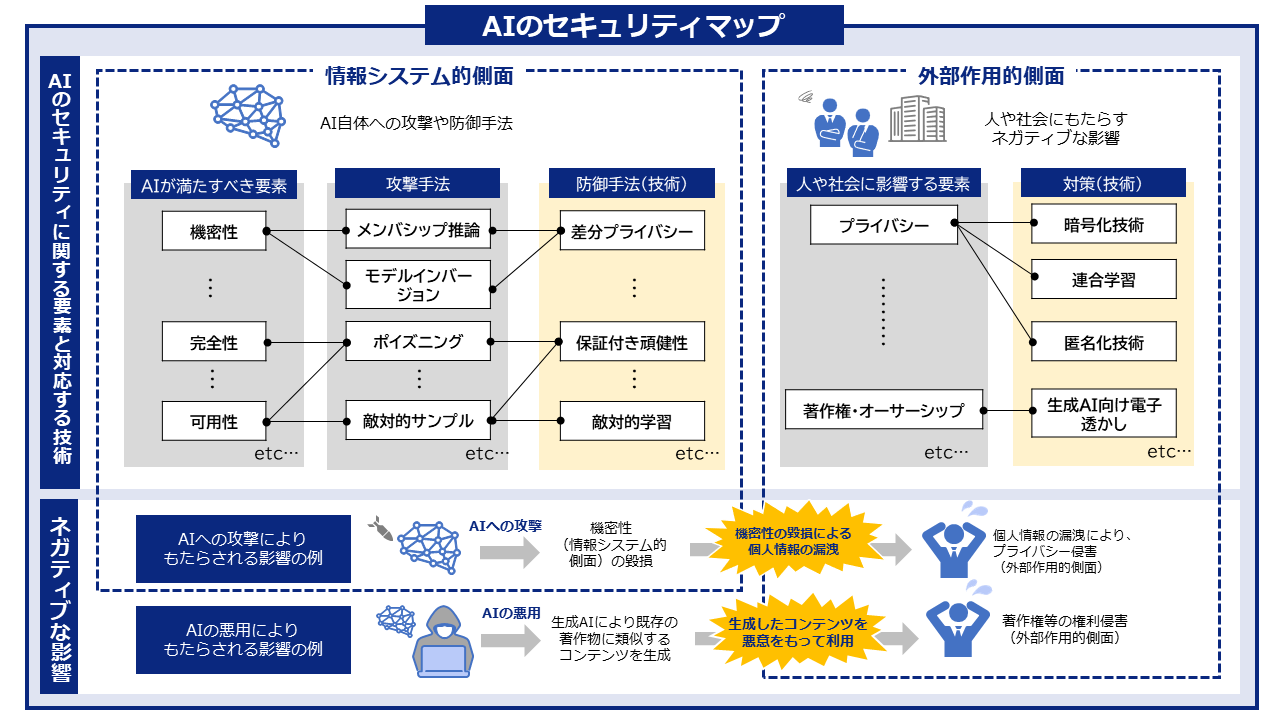
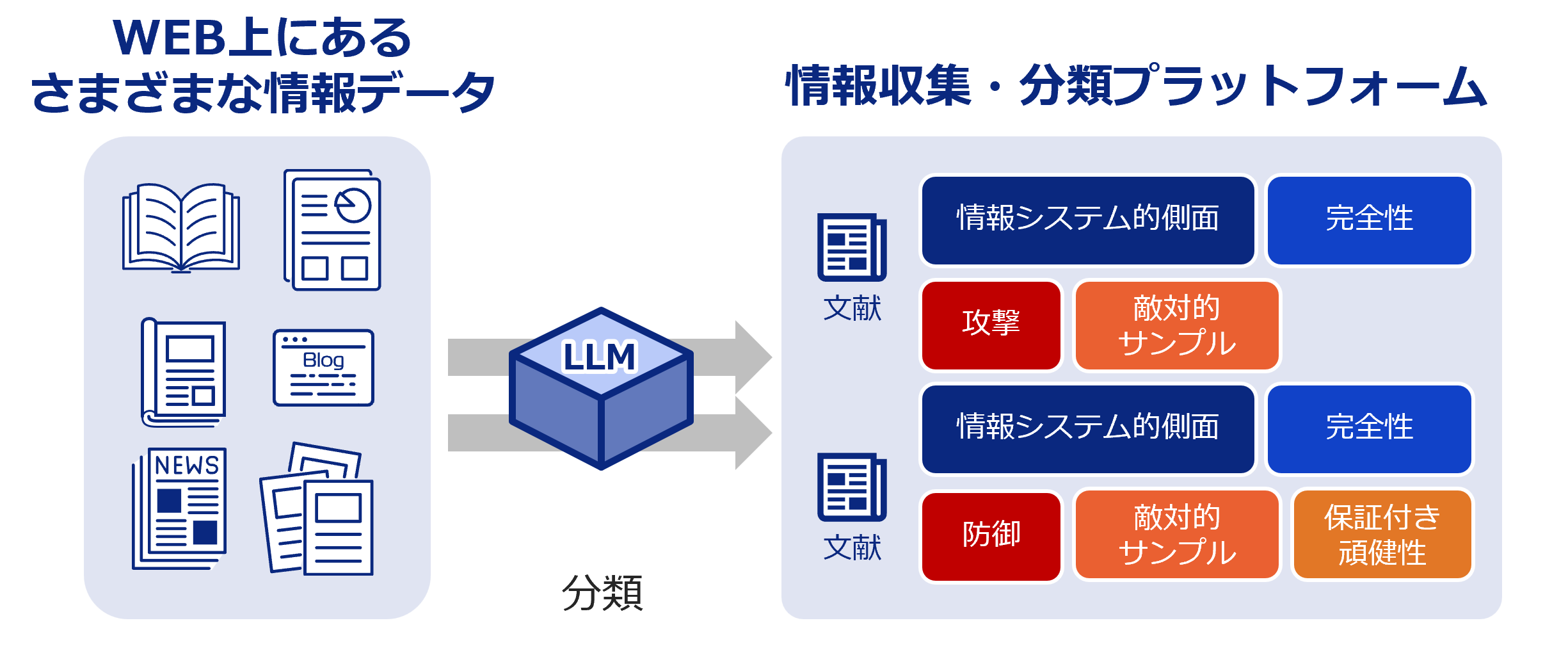
新着文献

David vs. Goliath: Verifiable Agent-to-Agent Jailbreaking via Reinforcement Learning
Authors: Samuel Nellessen, Tal Kachman | Published: 2026-02-02
2026.02.02

Guaranteeing Privacy in Hybrid Quantum Learning through Theoretical Mechanisms
Authors: Hoang M. Ngo, Tre’ R. Jeter, Incheol Shin, Wanli Xing, Tamer Kahveci, My T. Thai | Published: 2026-02-02
2026.02.02

Malware Detection Through Memory Analysis
Authors: Sarah Nassar | Published: 2026-02-02
2026.02.02

-scaled.png)