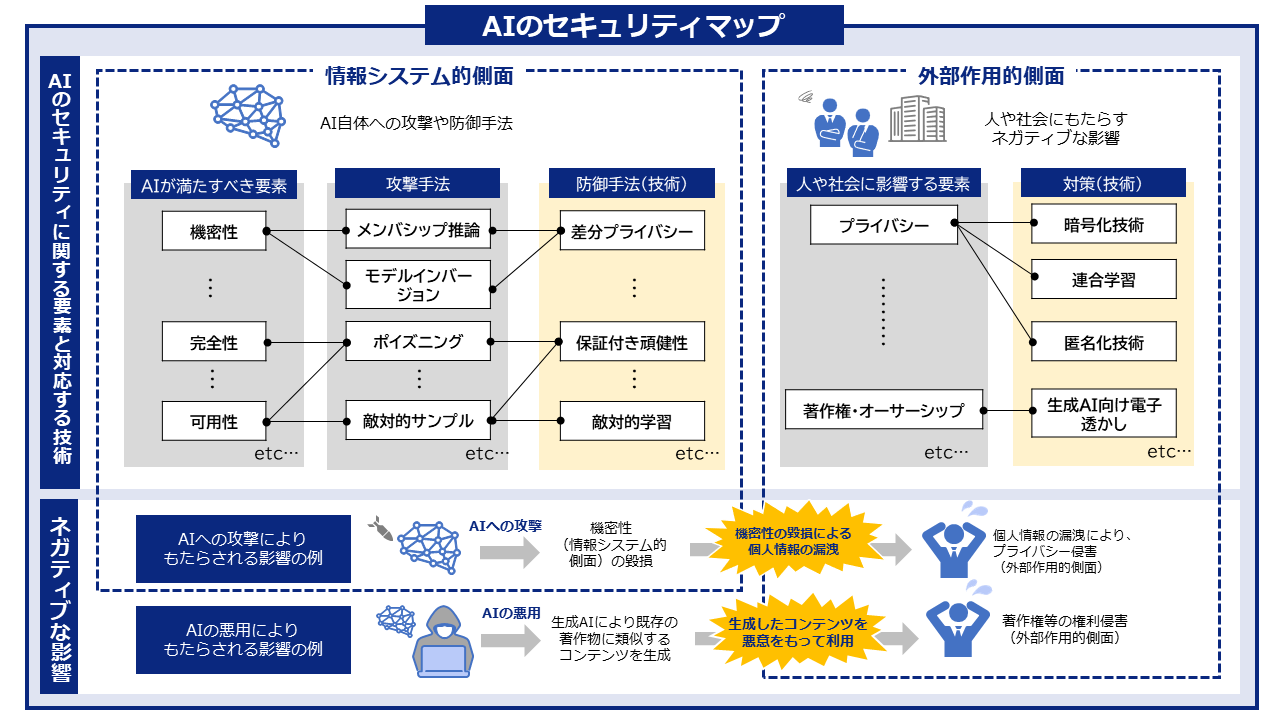
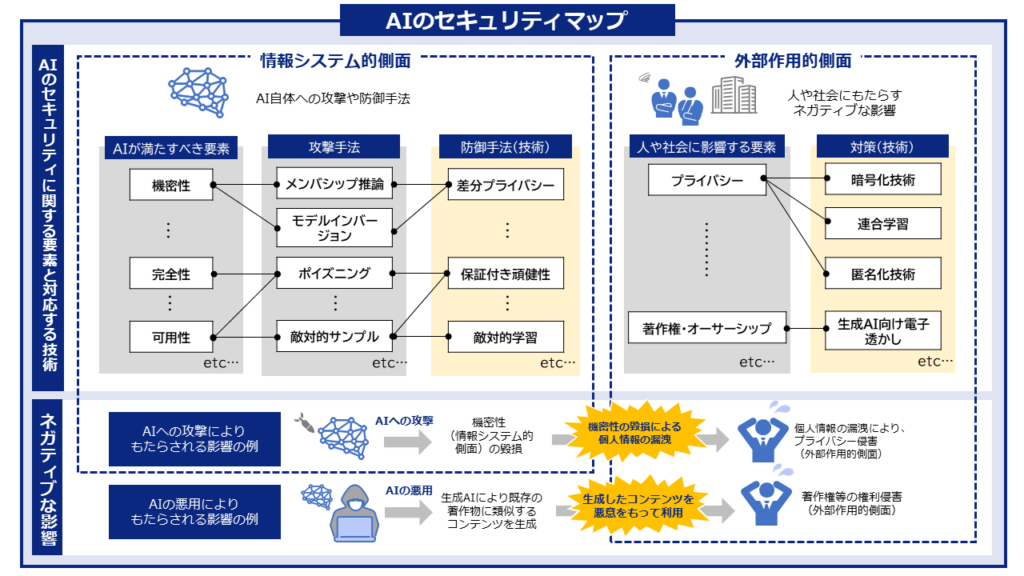
サイトコンテンツ
関連ニュース
最終更新日: 2026-01-30 06:02
-
ゼットスケーラー、ゼロトラスト基盤でAI活用を保護する「AI Security Suite」提供開始
2026-01-29 23:56 businessnetwork.jp -
2026年のサイバー攻撃はランサムウェアとAI詐欺が焦点、動向を踏まえた対策見直しが課題である
2026-01-29 23:18 act1.co.jp -
「pwn2own automotive 2026」に当社エンジニアの古川 和祈が出場しました | 脆弱性診断 ...
2026-01-29 17:54 gmo-cybersecurity.com -
「セキュリティ10大脅威2026」発表 - 多岐にわたる脅威「AIリスク」が初選出 - Security NEXT
2026-01-29 17:29 www.security-next.com -
「Security MOTION 2026 Spring」にて講演します | 株式会社NTTデータ先端技術
2026-01-28 15:48 www.intellilink.co.jp -
ランサムウェア対策を含む企業のサイバー防御を強化する、マイクロセグメンテーション ...
2026-01-28 12:32 prtimes.jp -
ランサムウェアが猛威を振るう、AI詐欺に注意…2026年「サイバー攻撃」で脅威となるのは何か ...
2026-01-28 06:05 news.yahoo.co.jp -
HPE OneViewの重大な脆弱性に対する活発な悪用を警告 組織は直ちにパッチ適用を
2026-01-26 06:30 www.fnn.jp -
AIエコノミー時代のセキュリティ予測 - 2026年は防御側が主導権を握る年
2026-01-26 04:30 news.mynavi.jp -
「Active Directory」狙う6つの攻撃、「Chrome拡張」のマルウェア化 知らぬ間に広がるリスク - IT
2026-01-24 09:14 atmarkit.itmedia.co.jp -
Android決済のAIセキュリティアーキテクチャ|数百ミリ秒で不正を検知する4層構造の全貌
2026-01-24 05:20 innovatopia.jp -
サイバー攻撃対応「しくじったら懲戒」 解雇妥当と考えるのはわずか5 - ITmedia
2026-01-23 10:21 www.itmedia.co.jp -
AIによる低品質な脆弱性レポート連発でcURLがバグ報奨金プログラムを停止 - GIGAZINE
2026-01-23 10:05 gigazine.net -
BIND 9の脆弱性対策について(CVE-2025-13878) | 情報セキュリティ - IPA
2026-01-23 07:25 www.ipa.go.jp -
ソフトウェア等の脆弱性関連情報に関する届出状況[2025年第4四半期(10月~12月)] - IPA
2026-01-22 09:04 www.ipa.go.jp -
プラバシー情報ダダ漏れを阻止。Windows 11のプライバシー設定の見直しガイド:Tech TIPS - IT
2026-01-21 06:47 atmarkit.itmedia.co.jp -
Check Point CloudGuard Network Security が Google Cloud Network Security Integration に統合
2026-01-20 11:02 s.netsecurity.ne.jp -
リモートアクセス型トロイの木馬「AsyncRAT」による多段階攻撃をMDRによって解明 - Trend Micro
2026-01-20 10:56 www.trendmicro.com -
2025年ランサムウェアは「想定外」ではなくなった--アサヒ、アスクルの被害が示す企業防御の現実
2026-01-20 10:01 japan.zdnet.com -
Security Management Conference Roadshow 東京 2026 冬 地政学リスク、経済安全保障
2026-01-20 07:00 www.tis.co.jp
※ この情報は、当ウェブサイトが設定したキーワードにもとづきGoogle Alertsの機能を利用して収集されたものです。これらの情報は第三者のウェブサイトやコンテンツから取得されており、その内容について当ウェブサイトは関与しておりません。
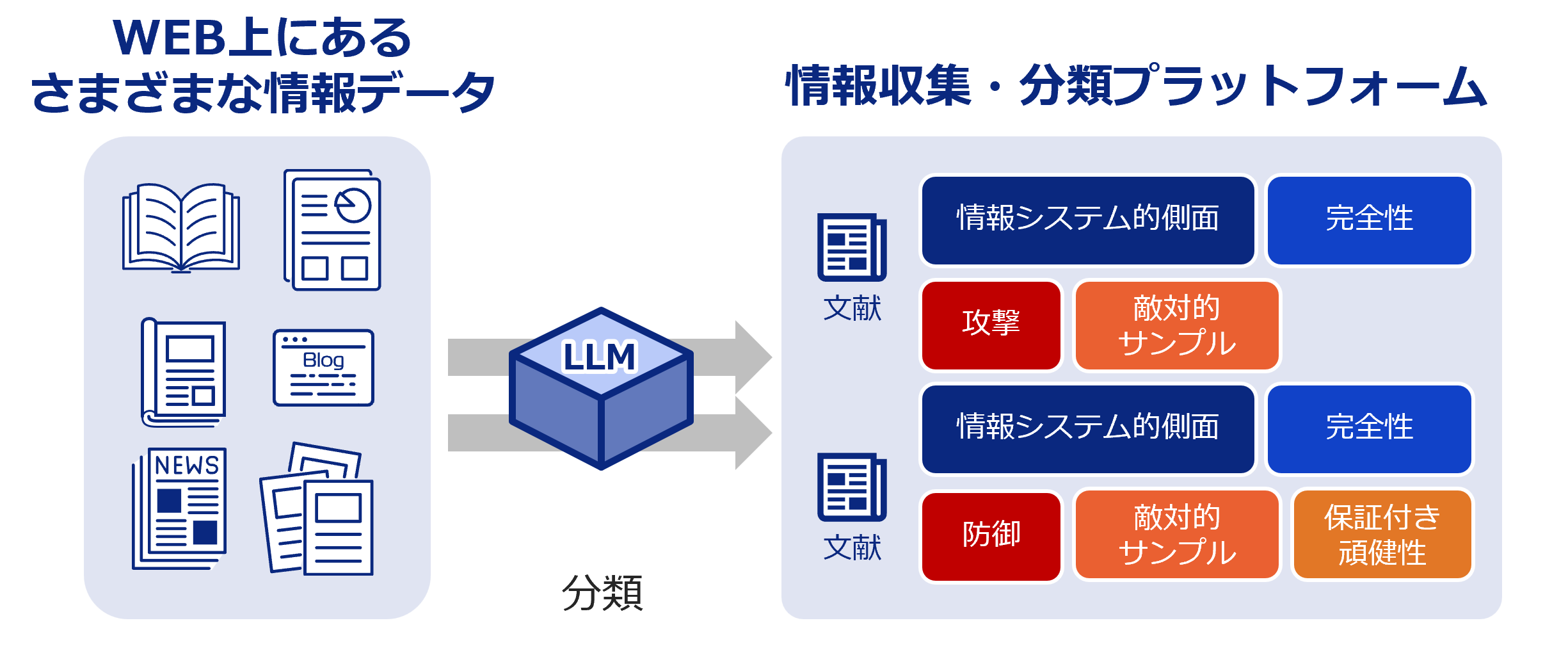
新着文献

IoT Device Identification with Machine Learning: Common Pitfalls and Best Practices
Authors: Kahraman Kostas, Rabia Yasa Kostas | Published: 2026-01-28
2026.01.28

Eliciting Least-to-Most Reasoning for Phishing URL Detection
Authors: Holly Trikilis, Pasindu Marasinghe, Fariza Rashid, Suranga Seneviratne | Published: 2026-01-28
2026.01.28

GAVEL: Towards rule-based safety through activation monitoring
Authors: Shir Rozenfeld, Rahul Pankajakshan, Itay Zloczower, Eyal Lenga, Gilad Gressel, Yisroel Mirsky | Published: 2026-01-27
2026.01.27

-scaled.png)