Site Contents
Related News
Last updated: 2025-12-14 06:00
-
Key takeaways | AI Governance and Security Assessment Workshop | JD Supra
2025-12-12 20:13 www.jdsupra.com -
AI code is creating security bottlenecks faster than it's solving them - SC Media
2025-12-12 19:40 www.scworld.com -
Red Hat Combines Kubernetes, Open Source AI, And Security For Enterprises
2025-12-11 19:26 www.opensourceforu.com -
SentinelOne remains undervalued despite transition to AI-native security platform: Citron
2025-12-11 18:21 www.msn.com -
2026 State of IT: Growth in AI, security, tech spending - Spiceworks
2025-12-11 18:21 www.spiceworks.com -
Security pros should prepare for tough questions on AI in 2026 - Computer Weekly
2025-12-10 20:08 www.computerweekly.com -
Raythink Ranks 9th in 2025 a&s Security 50, Showcasing AI-Driven Thermal Imaging ...
2025-12-06 19:32 finance.yahoo.com -
Rethinking the CIO-CISO Dynamic in the Age of AI - BankInfoSecurity
2025-12-06 15:39 www.bankinfosecurity.com -
New US National Security Strategy reveals Trump administration's latest stance on Taiwan
2025-12-06 15:38 defensescoop.com -
Live Webinar | Strategies to Address Emerging AI Security Needs with a Cloud-Centric ...
2025-12-05 19:57 www.bankinfosecurity.com -
Panaseer launches AI-powered suite to boost cybersecurity clarity - SecurityBrief UK
2025-12-05 19:54 securitybrief.co.uk -
Hack The Box launches AI cyber range & unveils red team certification - SecurityBrief UK
2025-12-05 19:54 securitybrief.co.uk -
The 10 Hottest Cybersecurity Startups Of 2025 - CRN
2025-12-05 19:05 www.crn.com -
How to Lead When Employees Are Worried About Job Security - Harvard Business Review
2025-12-05 17:56 hbr.org -
New infosec products of the week: December 5, 2025 - Help Net Security
2025-12-05 17:04 www.helpnetsecurity.com -
Microsoft 365 boosts prices in 2026 … to pay for more AI and security - The Register
2025-12-05 16:46 www.theregister.com -
An AI for an AI: Anthropic says AI agents require AI defense - The Register
2025-12-05 16:17 www.theregister.com -
Will National Security Demand Drive BigBear.ai's 2026 Revenue Cycle? - Yahoo Finance
2025-12-05 15:51 finance.yahoo.com -
MSSP Market News: Identity and AI Drive the Next Phase of Managed Security
2025-12-05 15:36 www.msspalert.com -
iOT365 rolls out unified OT security platform with native protocol discovery, automated CVE analysis
2025-12-05 15:03 industrialcyber.co
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
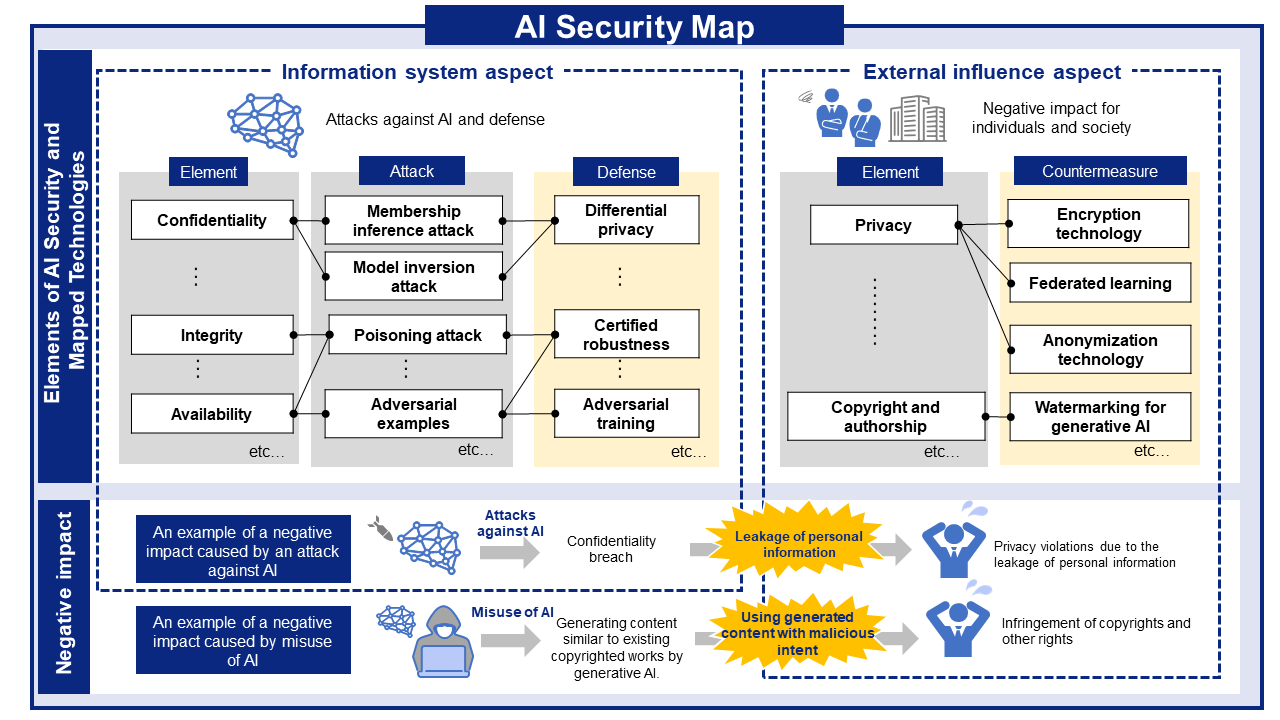
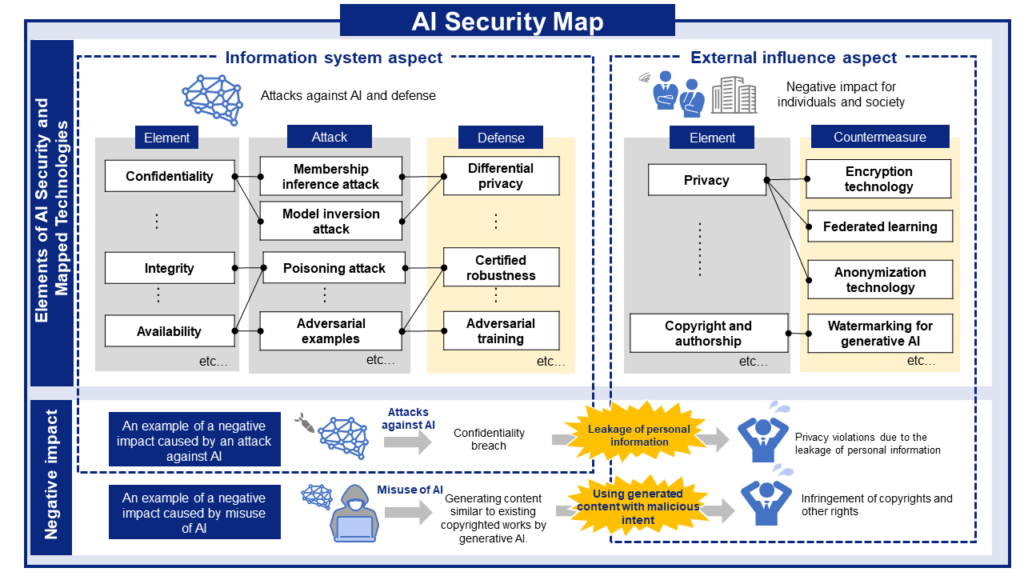
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
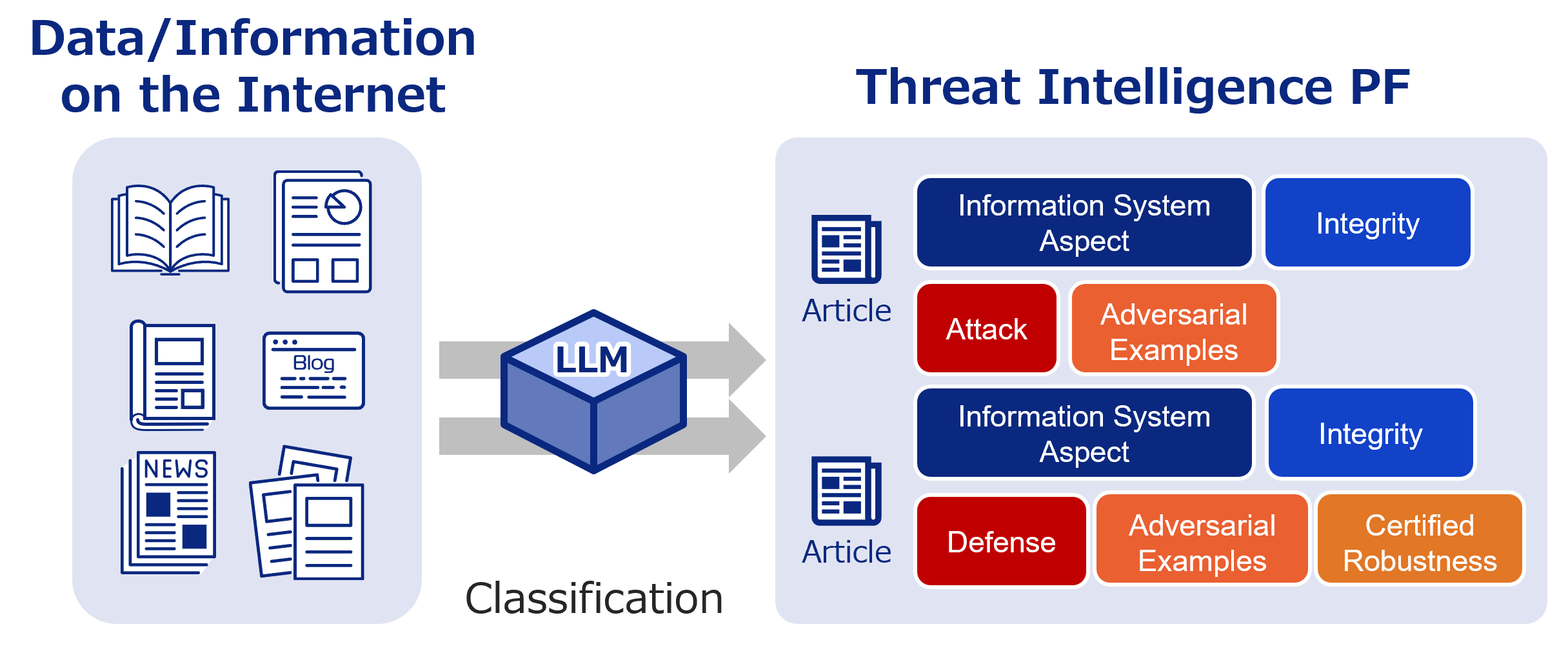
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

Virtual camera detection: Catching video injection attacks in remote biometric systems
Authors: Daniyar Kurmankhojayev, Andrei Shadrikov, Dmitrii Gordin, Mikhail Shkorin, Danijar Gabdullin, Aigerim Kambetbayeva, Kanat Kuatov | Published: 2025-12-11
2025.12.112025.12.13

TriDF: Evaluating Perception, Detection, and Hallucination for Interpretable DeepFake Detection
Authors: Jian-Yu Jiang-Lin, Kang-Yang Huang, Ling Zou, Ling Lo, Sheng-Ping Yang, Yu-Wen Tseng, Kun-Hsiang Lin, Chia-Ling Chen, Yu-Ting Ta, Yan-Tsung Wang, Po-Ching Chen, Hongxia Xie, Hong-Han Shuai, Wen-Huang Cheng | Published: 2025-12-11
2025.12.112025.12.13

LLM-Assisted AHP for Explainable Cyber Range Evaluation
Authors: Vyron Kampourakis, Georgios Kavallieratos, Georgios Spathoulas, Vasileios Gkioulos, Sokratis Katsikas | Published: 2025-12-11
2025.12.112025.12.13

-scaled.png)