Site Contents
Related News
Last updated: 2026-03-09 06:24
-
2 Top Cybersecurity Stocks to Buy in March - The Globe and Mail
2026-03-08 19:35 www.theglobeandmail.com -
Holding AI Accountable: Regulatory Gaps, Privacy Violations and Irish Law
2026-03-08 16:52 universitytimes.ie -
Anthropic Deemed a 'National Security Threat' - Is Palantir Technologies At Risk?
2026-03-08 14:23 247wallst.com -
AI Agent Exploits Security Flaws to Mine Cryptocurrency - Binance
2026-03-08 11:00 www.binance.com -
Study on rogue AI crypto‑mining agent resurfaces amid Alibaba AI security debate
2026-03-07 19:54 mlq.ai -
Trump's cyber strategy vows to 'support the security' of cryptocurrencies and blockchain
2026-03-07 19:50 www.coindesk.com -
Security for Microsoft 365 Copilot
2026-03-07 18:12 learn.microsoft.com -
Anthropic Vows Court Battle After Pentagon Flags AI Firm As Security Risk - YouTube
2026-03-07 16:51 www.youtube.com -
Great News: Zscaler Just Made a Bold AI Security Move - The Globe and Mail
2026-03-07 16:03 www.theglobeandmail.com -
Great News: Zscaler Just Made a Bold AI Security Move | The Motley Fool
2026-03-07 15:59 www.fool.com -
Anthropic's Claude AI uncovers over 100 security vulnerabilities in Firefox - The Decoder
2026-03-07 12:42 the-decoder.com -
AI Auditability: Why Leaders Must Prove How AI Makes Decisions - Security Boulevard
2026-03-07 11:33 securityboulevard.com -
OpenAI launches Codex Security, an AI agent designed to detect vulnerabilities in software projects
2026-03-06 19:53 the-decoder.com -
Claude AI Uncovers 22 Firefox Flaws in Security Partnership - The Tech Buzz
2026-03-06 19:39 www.techbuzz.ai -
Partnering with Mozilla to improve Firefox's security - Anthropic
2026-03-06 19:02 www.anthropic.com -
AI as tradecraft: How threat actors operationalize AI | Microsoft Security Blog
2026-03-06 18:07 www.microsoft.com -
Terra Security gains first AWS nod for AI threat tests - IT Brief Asia
2026-03-06 16:15 itbrief.asia -
AI, workers, and national security in a changing world: A conversation with Sen. Mark Kelly
2026-03-06 16:02 www.brookings.edu -
AICM Rolls Out AI Security Ahead of World Cup 2026 - Mexico Business News
2026-03-06 15:38 mexicobusiness.news -
Pentagon flags AI firm as security risk | Fingerlakes1.com
2026-03-06 15:36 www.fingerlakes1.com
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
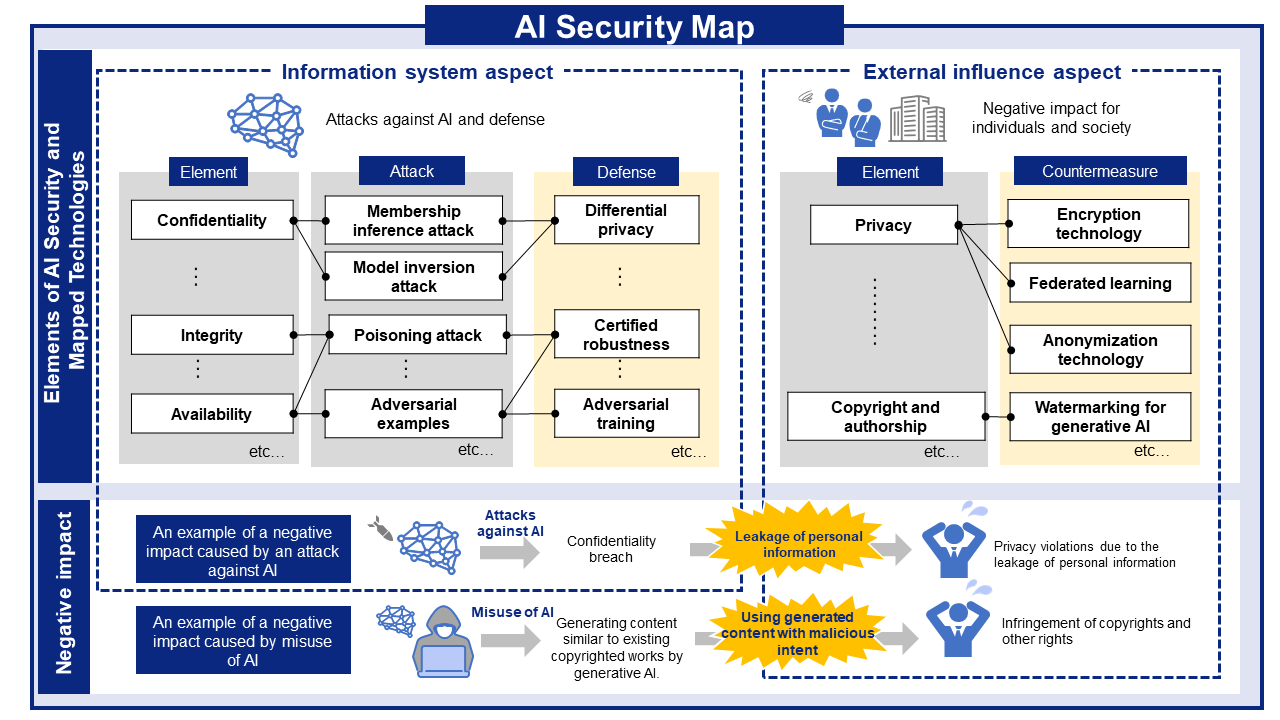
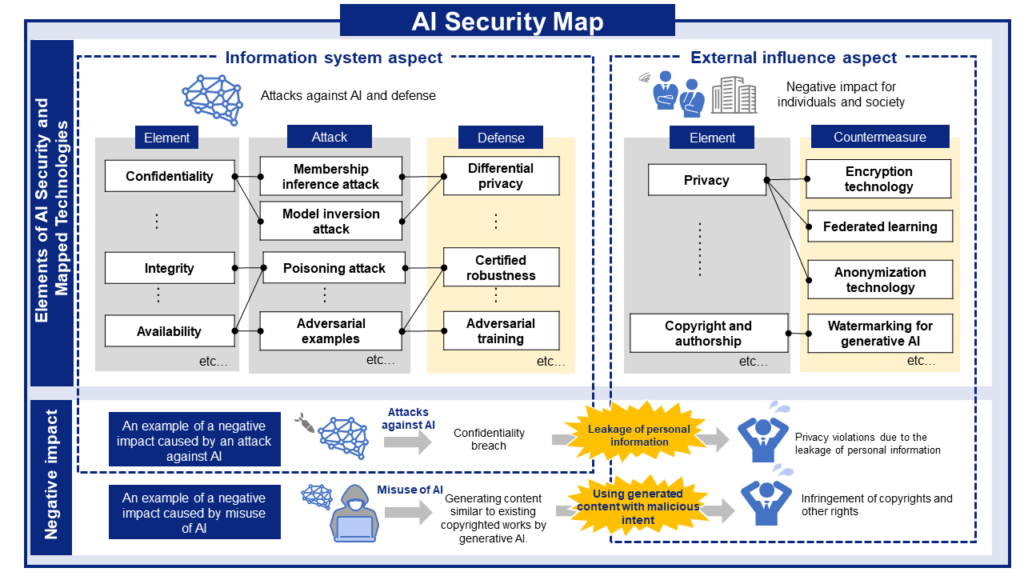
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
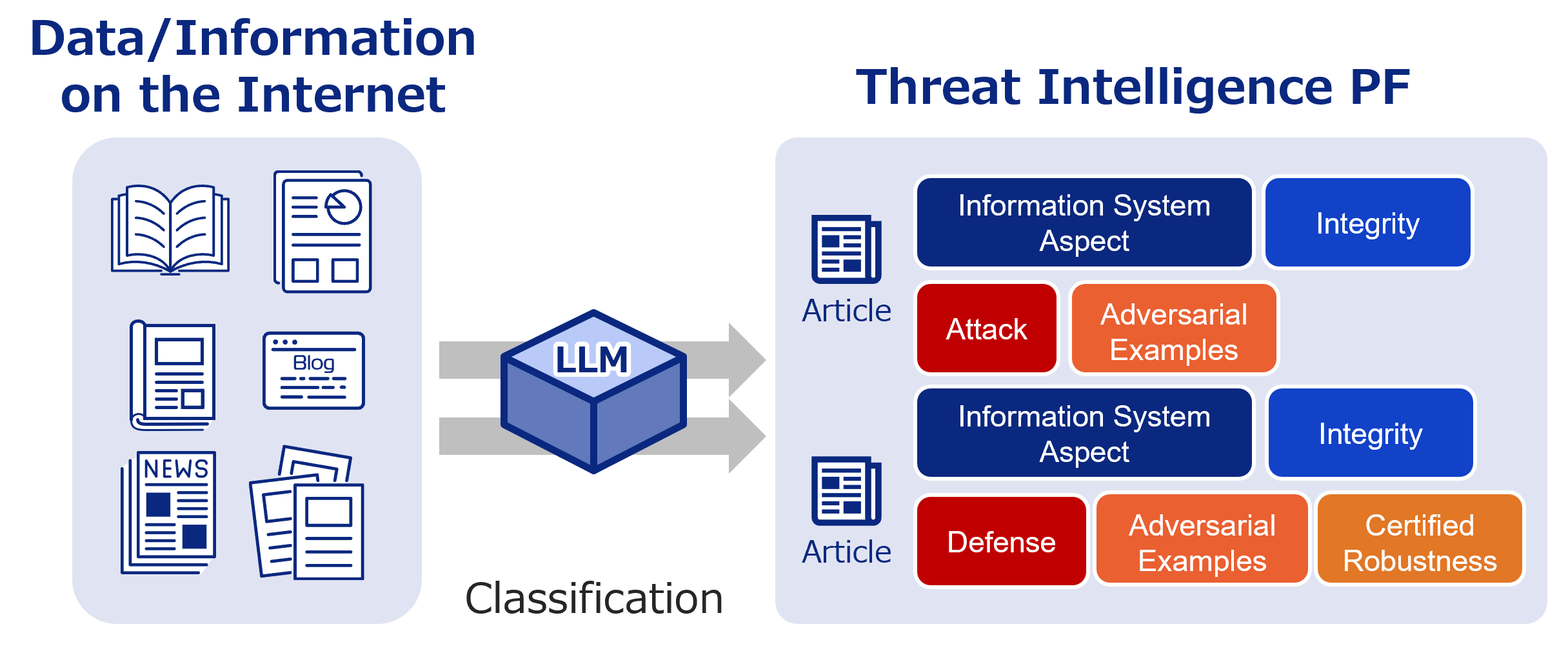
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

Lambda-randomization: multi-dimensional randomized response made easy
Authors: Nicolas Ruiz | Published: 2026-03-05
2026.03.052026.03.07

Good-Enough LLM Obfuscation (GELO)
Authors: Anatoly Belikov, Ilya Fedotov | Published: 2026-03-05
2026.03.052026.03.07

Efficient Privacy-Preserving Sparse Matrix-Vector Multiplication Using Homomorphic Encryption
Authors: Yang Gao, Gang Quan, Wujie Wen, Scott Piersall, Qian Lou, Liqiang Wang | Published: 2026-03-05
2026.03.052026.03.07

-scaled.png)