Site Contents
Related News
Last updated: 2026-02-25 06:04
-
AI Rattles Cybersecurity Markets: What Anthropic's Code Security Actually Does - Forbes
2026-02-25 04:38 www.forbes.com -
AI-Powered Threats vs. AI-Powered Defenses: Winning the Cybersecurity Arms Race in 2026
2026-02-25 04:36 www.msspalert.com -
Trust and transparency critical in cloud AI security - SC Media
2026-02-25 04:24 www.scworld.com -
Center for Critical Infrastructure Security Awarded Maryland Cyber & AI Clinic Grant
2026-02-25 04:20 www.hstoday.us -
Meta Security Researcher's AI Agent Accidentally Deleted Her Emails - PCMag UK
2026-02-25 02:46 uk.pcmag.com -
AI Security in Azure with Microsoft Defender for Cloud: Learn the How, Join the Session
2026-02-25 02:23 techcommunity.microsoft.com -
Cisco Live EMEA Recap: Turning AI Security into Partner Growth
2026-02-25 01:18 blogs.cisco.com -
Harness launches Artifact Registry with AI security controls - Techzine Global
2026-02-25 01:08 www.techzine.eu -
The Cyber-Resilient CISO Virtual Summit 2026 - Infosecurity Magazine
2026-02-25 00:54 www.infosecurity-magazine.com -
Microsoft Security Dashboard Strengthens Control Over Expanding AI Ecosystems
2026-02-25 00:32 cloudwars.com -
Zscaler Stock Scales Zero Trust And AI Agent Security (NASDAQ:ZS) | Seeking Alpha
2026-02-25 00:25 seekingalpha.com -
Identity-First AI Security: Why CISOs Must Add Intent to the Equation - Bleeping Computer
2026-02-25 00:13 www.bleepingcomputer.com -
Cybersecurity stock selling deepens on AI threat concerns. Why we're not bailing - CNBC
2026-02-23 20:21 www.cnbc.com -
Cybersecurity Stocks Crater on AI Fears - But Hold On | The Tech Buzz
2026-02-23 20:17 www.techbuzz.ai -
Anthropic's AI Bug Hunter Jolts Cyber Stocks - GovInfoSecurity
2026-02-22 17:46 www.govinfosecurity.com -
Cybersecurity stocks drop after Anthropic debuts Claude Code Security - SiliconANGLE
2026-02-21 20:06 siliconangle.com -
Anthropic's AI security tool just found 500 bugs humans missed, and Wall Street panicked
2026-02-21 17:21 www.cryptopolitan.com -
One AI Tweet, $10 Billion Gone: Is Cyber Security in Trouble? - Gulte
2026-02-21 16:27 www.gulte.com -
Agentic AI security: Prompt injection and manipulation attacks - Microsoft Community Hub
2026-02-20 20:02 techcommunity.microsoft.com -
'God-Like' Attack Machines: AI Agents Ignore Security Policies - Dark Reading
2026-02-20 18:41 www.darkreading.com
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
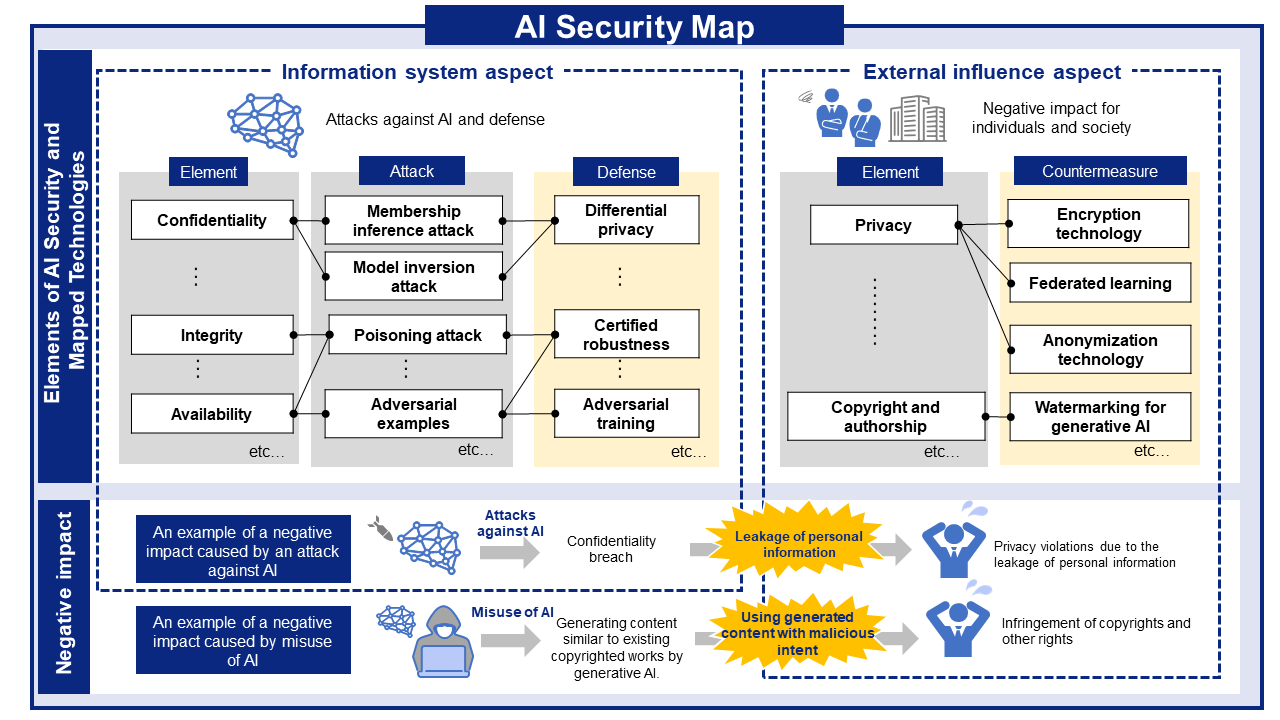
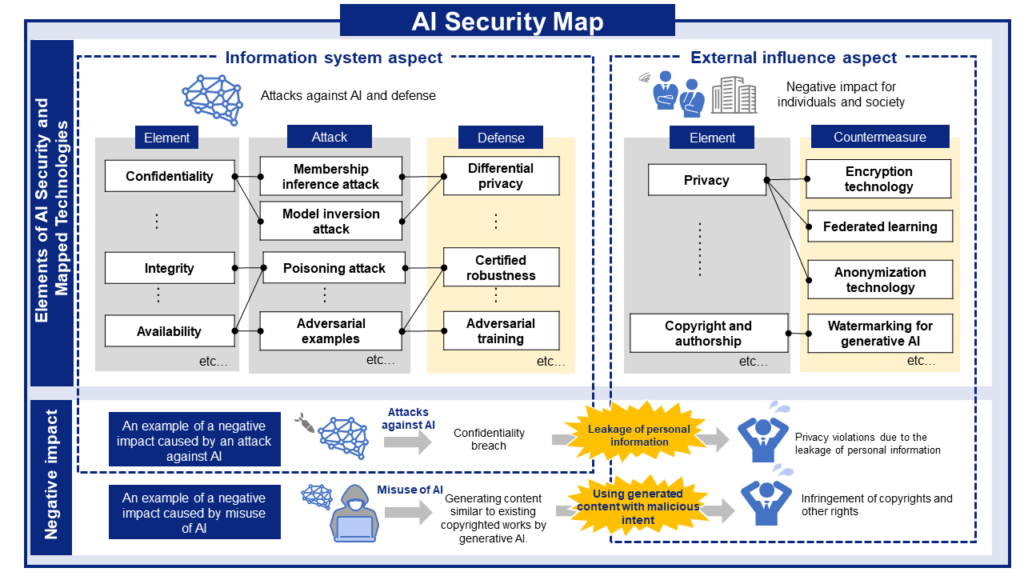
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
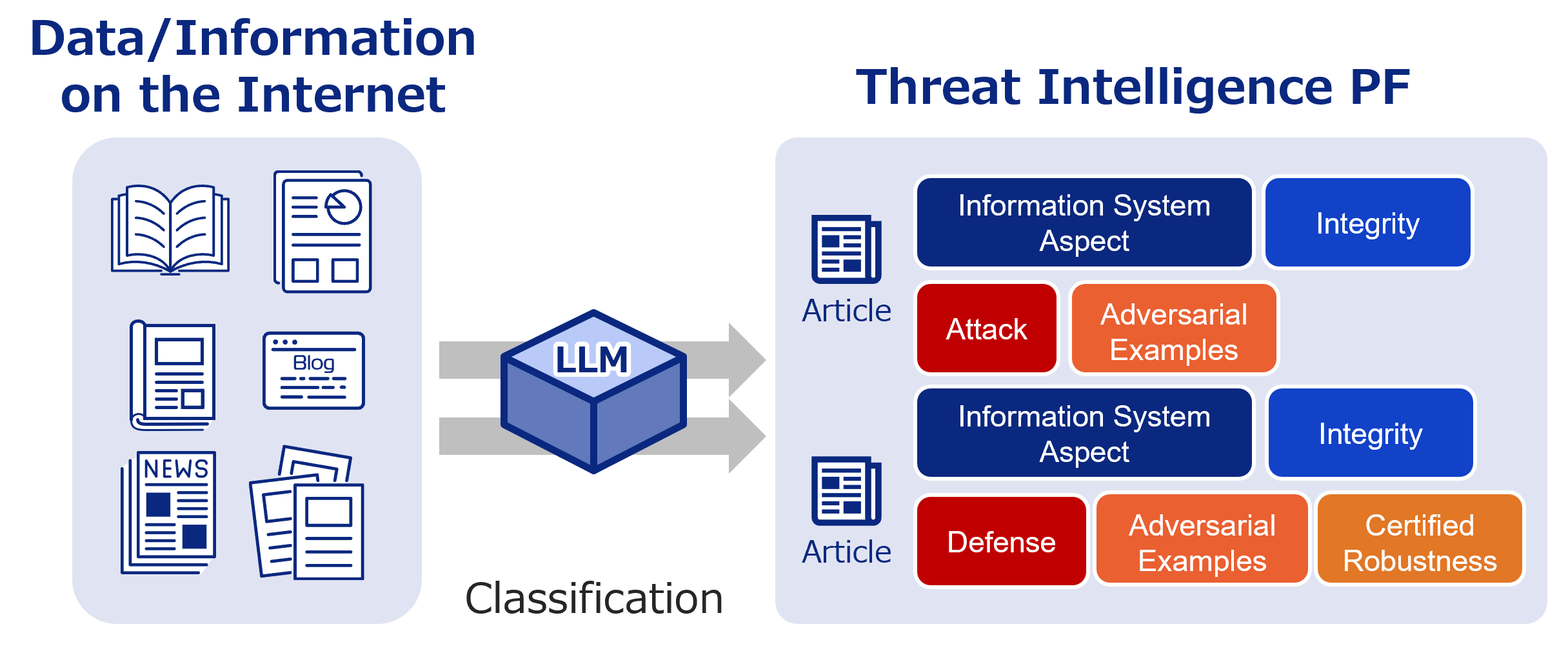
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

The LLMbda Calculus: AI Agents, Conversations, and Information Flow
Authors: Zac Garby, Andrew D. Gordon, David Sands | Published: 2026-02-23
2026.02.232026.02.25

Can You Tell It’s AI? Human Perception of Synthetic Voices in Vishing Scenarios
Authors: Zoha Hayat Bhatti, Bakhtawar Ahtisham, Seemal Tausif, Niklas George, Nida ul Habib Bajwa, Mobin Javed | Published: 2026-02-23
2026.02.232026.02.25

RobPI: Robust Private Inference against Malicious Client
Authors: Jiaqi Xue, Mengxin Zheng, Qian Lou | Published: 2026-02-23
2026.02.232026.02.25

-scaled.png)