Site Contents
Related News
Last updated: 2026-02-23 06:00
-
Anthropic's AI Bug Hunter Jolts Cyber Stocks - GovInfoSecurity
2026-02-23 02:46 www.govinfosecurity.com -
Cybersecurity stocks drop after Anthropic debuts Claude Code Security - SiliconANGLE
2026-02-21 20:06 siliconangle.com -
Anthropic's AI security tool just found 500 bugs humans missed, and Wall Street panicked
2026-02-21 17:21 www.cryptopolitan.com -
One AI Tweet, $10 Billion Gone: Is Cyber Security in Trouble? - Gulte
2026-02-21 16:27 www.gulte.com -
Agentic AI security: Prompt injection and manipulation attacks - Microsoft Community Hub
2026-02-20 20:02 techcommunity.microsoft.com -
'God-Like' Attack Machines: AI Agents Ignore Security Policies - Dark Reading
2026-02-20 18:41 www.darkreading.com -
The AI security nightmare is here and it looks suspiciously like lobster | The Verge
2026-02-19 19:02 www.theverge.com -
CrowdStrike (CRWD) Valuation Check After HSBC Upgrade And Renewed AI Security Optimism
2026-02-15 18:48 simplywall.st -
Homeland security pushes social media giants to dox anonymous accounts critical of ICE
2026-02-15 15:45 mashable.com -
ISMG Editors: CISA Turmoil Raises Cyber Defense Concerns - BankInfoSecurity
2026-02-15 15:28 www.bankinfosecurity.com -
Backslash Security: $19 Million Series A Raised For Protecting AI-Driven Software Development
2026-02-15 14:26 pulse2.com -
'Crazy' Hackers Strike Through Remote Monitoring Software - BankInfoSecurity
2026-02-15 13:56 www.bankinfosecurity.com -
Social Links Launches AI Agent Security Platform to Combat AI Fraud Crisis - Florida Today
2026-02-15 13:10 www.floridatoday.com -
Security flaws expose 'vibe-coding' AI platform Orchids to easy hacking
2026-02-15 12:55 dig.watch -
Enkrypt AI Launches Enkrypt AI Academy to Advance Enterprise AI Security Education
2026-02-15 11:43 www.floridatoday.com -
Proofpoint acquires Acuvity to deliver AI security - IOT Insider
2026-02-15 11:05 www.iotinsider.com -
Homeland Security reportedly sent hundreds of subpoenas seeking to unmask anti-ICE accounts
2026-02-15 10:31 techcrunch.com -
Inside a $15 Million Mansion Designed Entirely Around Security - WSJ.com
2026-02-14 20:02 www.wsj.com -
Microsoft Added AI to Notepad and It Created a Security Failure Because the AI Was ... - Futurism
2026-02-14 18:32 futurism.com -
PureCipher Responds to Moltbook AI Agent Security Concerns with Artificial Immune ...
2026-02-14 18:27 www.floridatoday.com
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
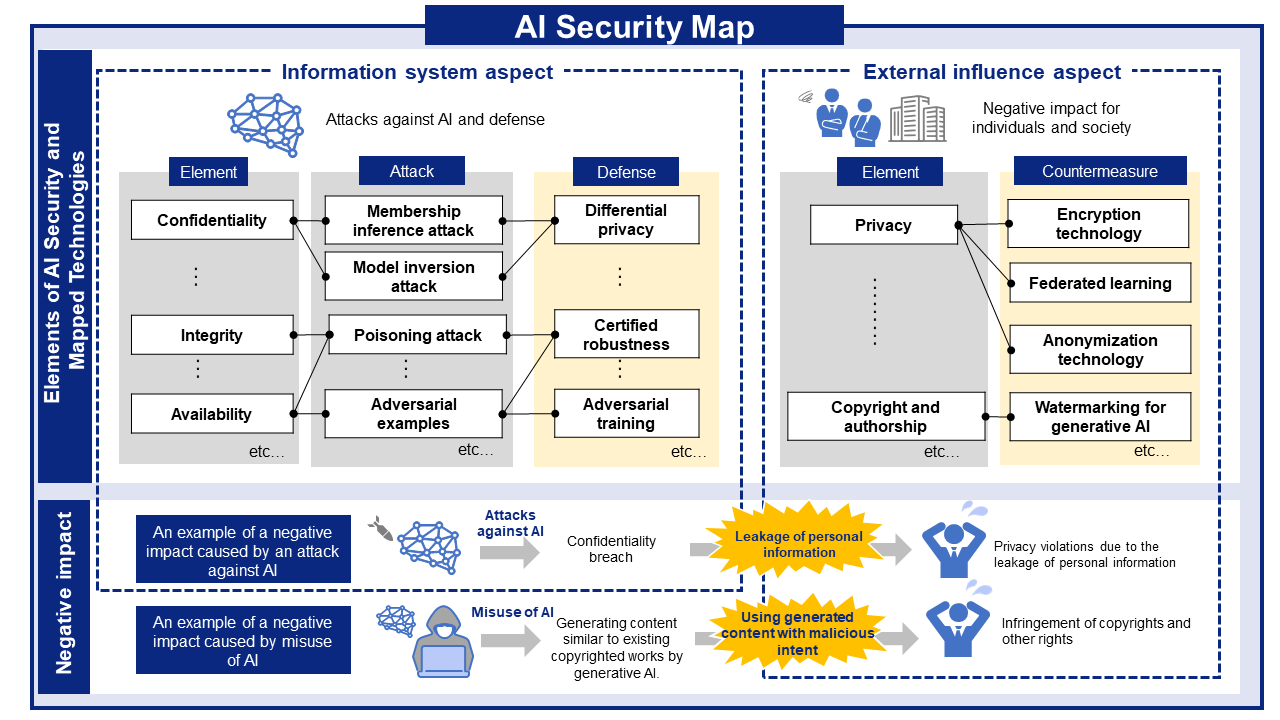
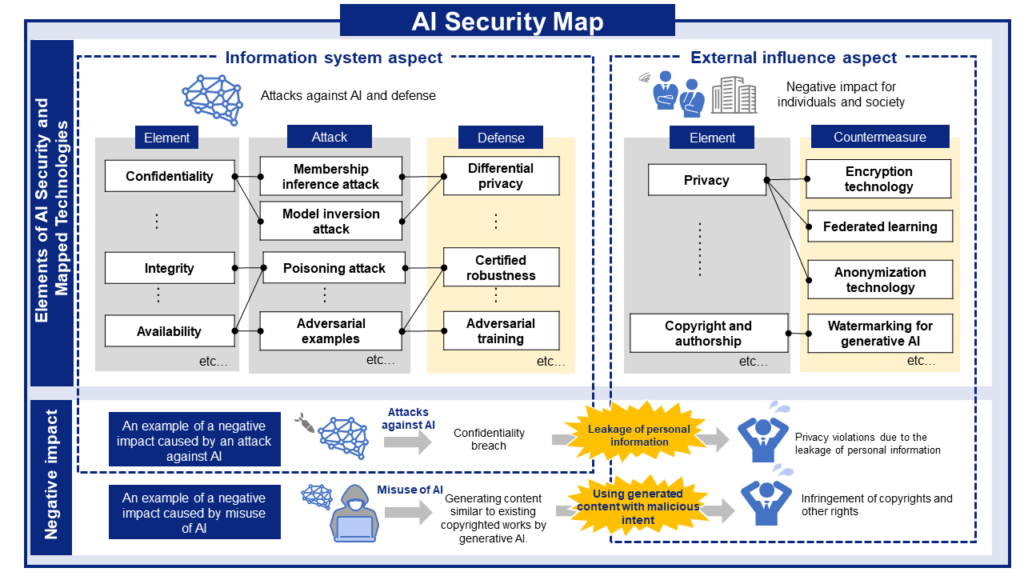
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
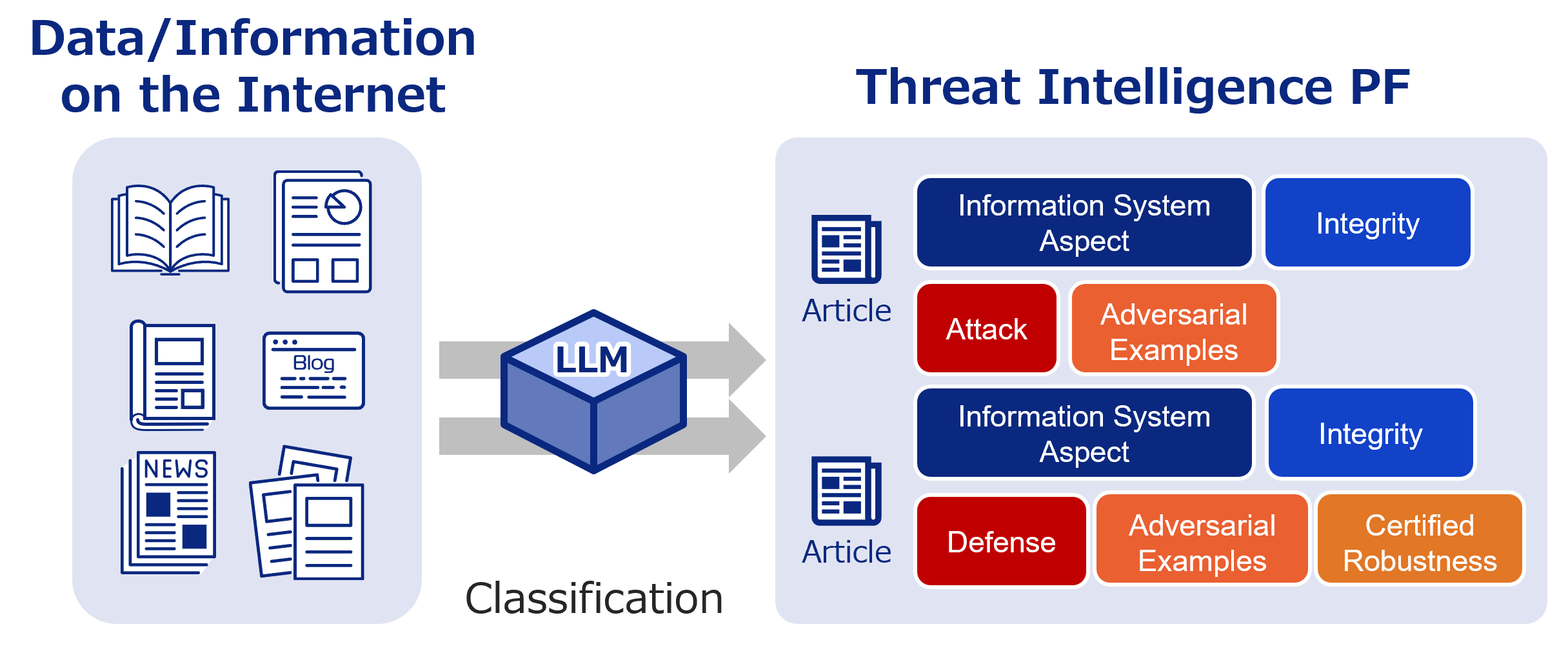
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

Jolt Atlas: Verifiable Inference via Lookup Arguments in Zero Knowledge
Authors: Wyatt Benno, Alberto Centelles, Antoine Douchet, Khalil Gibran | Published: 2026-02-19
2026.02.192026.02.21

What Breaks Embodied AI Security:LLM Vulnerabilities, CPS Flaws,or Something Else?
Authors: Boyang Ma, Hechuan Guo, Peizhuo Lv, Minghui Xu, Xuelong Dai, YeChao Zhang, Yijun Yang, Yue Zhang | Published: 2026-02-19
2026.02.192026.02.21

Privacy-Preserving Mechanisms Enable Cheap Verifiable Inference of LLMs
Authors: Arka Pal, Louai Zahran, William Gvozdjak, Akilesh Potti, Micah Goldblum | Published: 2026-02-19
2026.02.192026.02.21

-scaled.png)