Site Contents
Related News
Last updated: 2026-01-17 06:03
-
Senate passes more spending bills, but Homeland Security dispute looms
2026-01-17 04:42 federalnewsnetwork.com -
AI and the Corporate Capture of Knowledge - Schneier on Security
2026-01-17 04:12 www.schneier.com -
Adaptability is the new job security and 4 more future AI trends from EY's global chief ...
2026-01-17 03:01 fortune.com -
Agentic Browser Security: 2025 Year-End Review | Wiz Blog
2026-01-17 02:50 www.wiz.io -
Legal Brief: Generative AI and Privacy Clash | Security Info Watch
2026-01-17 02:04 www.securityinfowatch.com -
CEOs, security executives are divided on cyber risks of AI, survey finds - OODAloop
2026-01-17 01:53 oodaloop.com -
Architecture of Agentic Defense: Inside the Falcon Platform - CrowdStrike
2026-01-17 01:50 www.crowdstrike.com -
Feature Article Examines AI Use in Modern Network Security - EIN Presswire
2026-01-17 01:47 www.einpresswire.com -
Radware (RDWR) Valuation Check After ZombieAgent AI Security Discovery
2026-01-17 01:42 simplywall.st -
From AI Coding to QR Code Scams, 2026 Is Already a Security Nightmare - PCMag UK
2026-01-17 01:36 uk.pcmag.com -
CISA Issues New AI Security Guidance for Critical Infrastructure - TechRepublic
2026-01-15 20:56 www.techrepublic.com -
Depthfirst raises $40 million for AI-powered security platform | SC Media
2026-01-15 18:12 www.scworld.com -
Key Trends that Will Shape Tech Policy in 2026 - Just Security
2026-01-15 18:07 www.justsecurity.org -
Accel Backs AI Security Startup in $40M Series A - Bloomberg.com
2026-01-14 19:46 www.bloomberg.com -
Key facts: Cisco focuses on AI security in Middle East; DinéLink wins award - TradingView
2026-01-13 20:15 www.tradingview.com -
Video of Nicolás Maduro being escorted by US security officers is AI-generated - Yahoo
2026-01-13 19:37 www.yahoo.com -
How Microsoft builds privacy and security to work hand-in-hand | Microsoft Security Blog
2026-01-13 18:49 www.microsoft.com -
Investors Shift Focus to AI Infrastructure, Security and Commerce | PYMNTS.com
2026-01-12 19:52 www.pymnts.com -
The 20 Coolest Cloud Security Companies Of The 2026 Cloud 100 - CRN
2026-01-12 19:49 www.crn.com -
AI Adoption Leaves Cloud Security Struggling To Keep Up, Report Finds - BusinessToday
2026-01-10 19:50 www.businesstoday.com.my
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
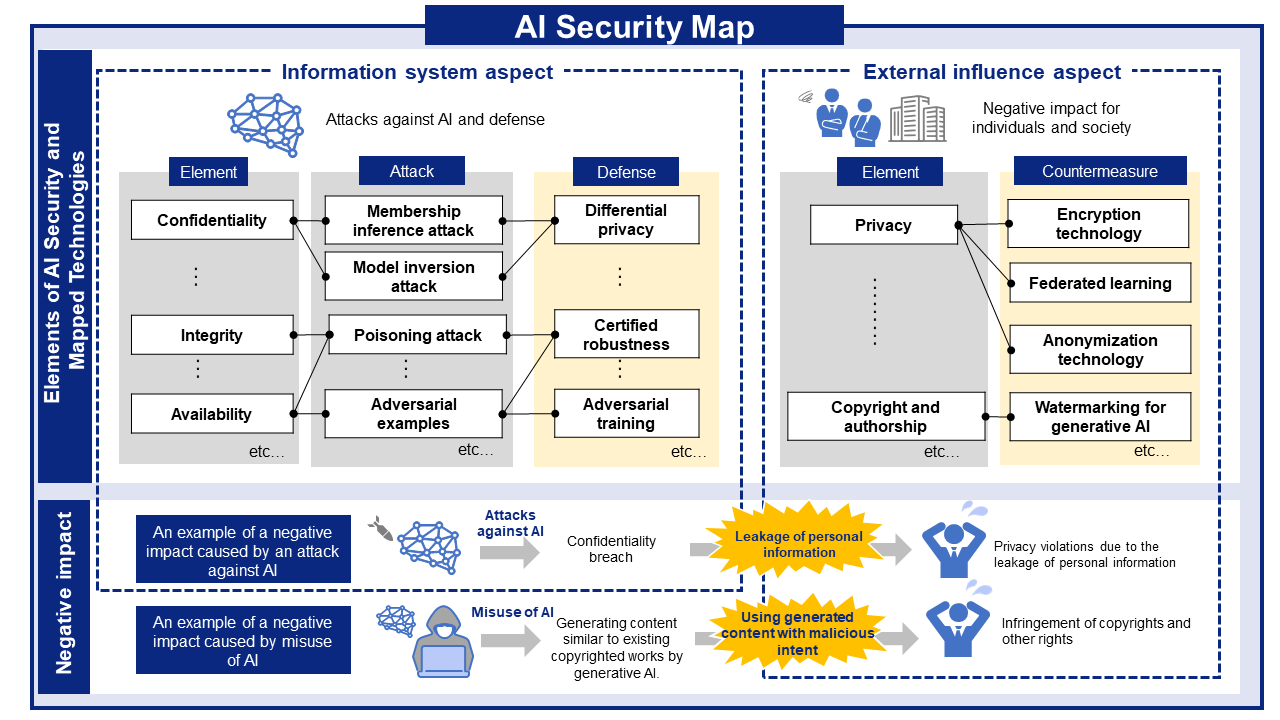
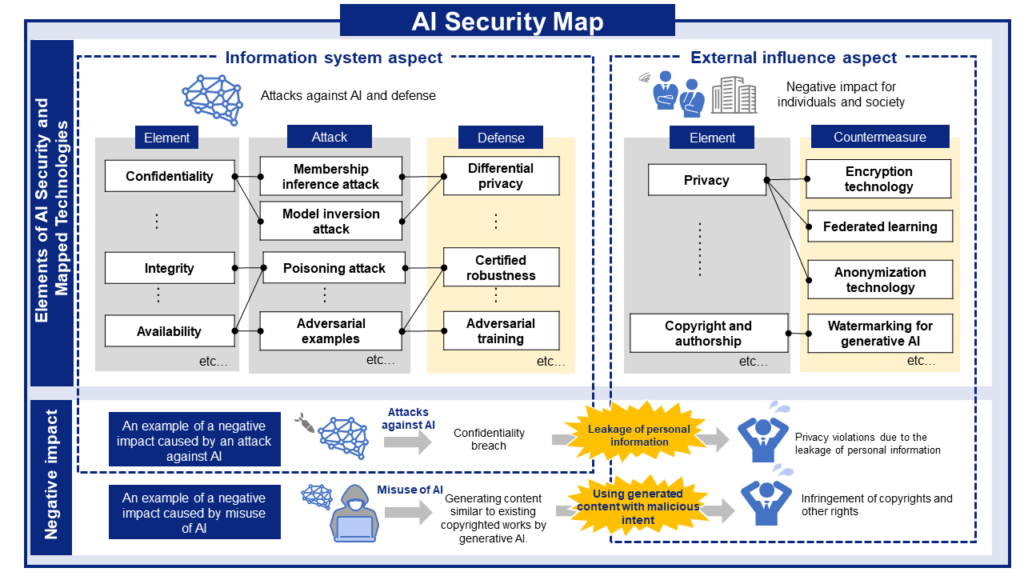
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
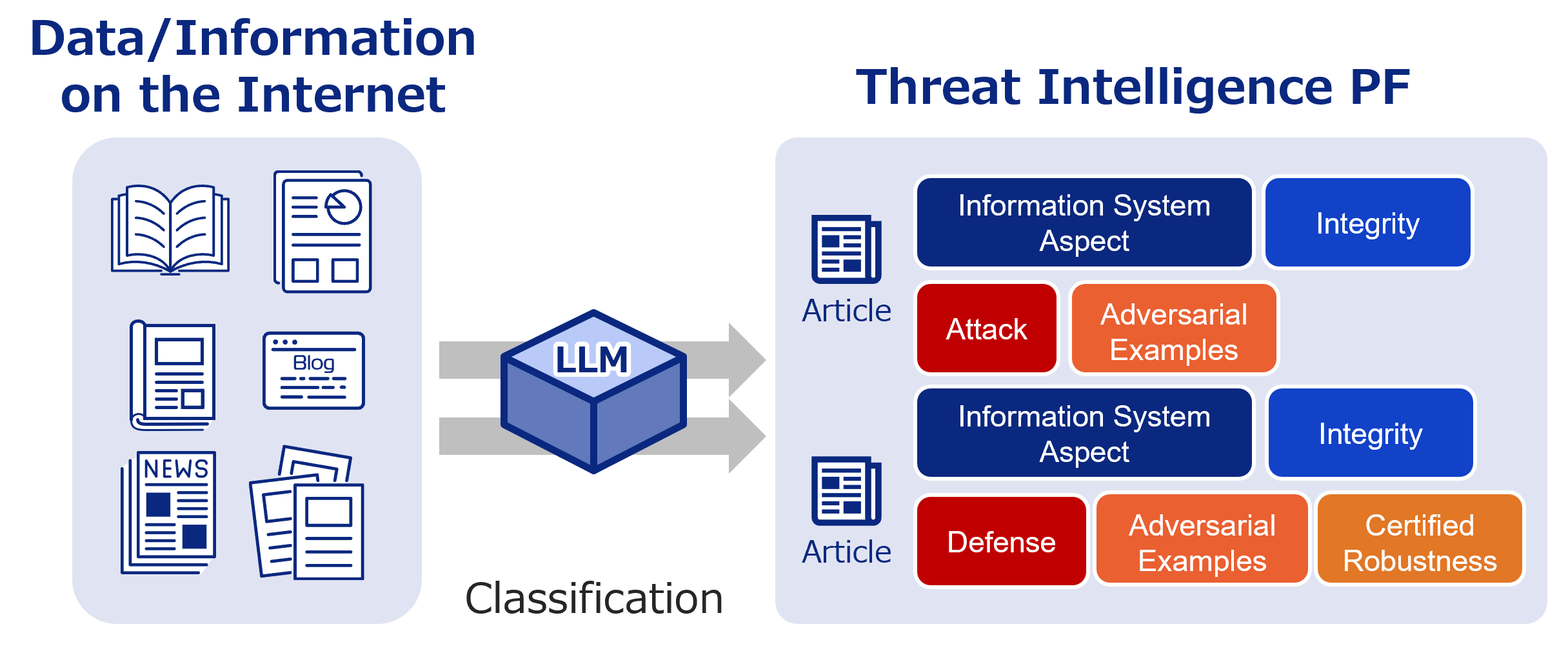
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

Be Your Own Red Teamer: Safety Alignment via Self-Play and Reflective Experience Replay
Authors: Hao Wang, Yanting Wang, Hao Li, Rui Li, Lei Sha | Published: 2026-01-15
2026.01.152026.01.17

LADFA: A Framework of Using Large Language Models and Retrieval-Augmented Generation for Personal Data Flow Analysis in Privacy Policies
Authors: Haiyue Yuan, Nikolay Matyunin, Ali Raza, Shujun Li | Published: 2026-01-15
2026.01.152026.01.17

ReasAlign: Reasoning Enhanced Safety Alignment against Prompt Injection Attack
Authors: Hao Li, Yankai Yang, G. Edward Suh, Ning Zhang, Chaowei Xiao | Published: 2026-01-15
2026.01.152026.01.17

-scaled.png)