Site Contents
Related News
Last updated: 2026-01-09 06:01
-
CrowdStrike to buy identity security startup SGNL for $740 million to tackle AI threats
2026-01-09 04:39 finance.yahoo.com -
What happens to insider risk when AI becomes a coworker - Help Net Security
2026-01-09 03:03 www.helpnetsecurity.com -
Google Chrome 143 Security Bypass — 3 Billion Users At Risk - Forbes
2026-01-09 02:48 www.forbes.com -
AI security boom triples valuation of Israeli cyber startup to $9 billion within a year
2026-01-09 02:20 www.timesofisrael.com -
When AI agents interact, risk can emerge without warning - Help Net Security
2026-01-07 18:30 www.helpnetsecurity.com -
Reolink made a local AI hub for its security cameras | The Verge
2026-01-06 20:01 www.theverge.com -
Introducing the Microsoft Defender Experts Suite: Elevate your security with expert-led services
2026-01-06 18:08 www.microsoft.com -
As AI Moves Into Government, National Security Enters A New Era In 2026 - Forbes
2026-01-05 19:48 www.forbes.com -
OTOPIQ launches AI-driven zero-trust OT security firm - SecurityBrief Asia
2026-01-05 19:37 securitybrief.asia -
Cybersecurity leaders' resolutions for 2026 - CSO Online
2026-01-05 19:02 www.csoonline.com -
AI in Higher Education: Protecting Student Data Privacy | EdTech Magazine
2026-01-05 18:20 edtechmagazine.com -
Tech Trends: What States Should Fund With 2026 Cybersecurity Grants
2026-01-05 17:58 statetechmagazine.com -
From SBOM to AI BOM: Rethinking supply chain security for AI native software - SD Times
2026-01-05 17:34 sdtimes.com -
Auto-ISAC, Google partner to boost automotive sector cybersecurity | Google Cloud Blog
2026-01-05 17:20 cloud.google.com -
Navigate the Money Matrix in Our Upcoming Series: Privacy, Security, and AI Explained
2026-01-05 16:37 www.troutman.com -
Navigate the Money Matrix in Our Upcoming Series: Privacy, Security, and AI Explained
2026-01-05 16:19 www.jdsupra.com -
Getting the right security in place for Agentic AI - SmartBrief
2026-01-05 16:05 www.smartbrief.com -
Cyclotron Expands Offshore Hiring to Accelerate Client Success in AI, Azure, Security, and ...
2026-01-05 15:20 techrseries.com -
AI Dominates Cybersecurity Predictions for 2026 - TechNewsWorld
2026-01-05 15:02 www.technewsworld.com -
Grok AI Security Lapse Leads to Generation of Child Abuse Material on X | IBTimes UK
2026-01-04 16:28 www.ibtimes.co.uk
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
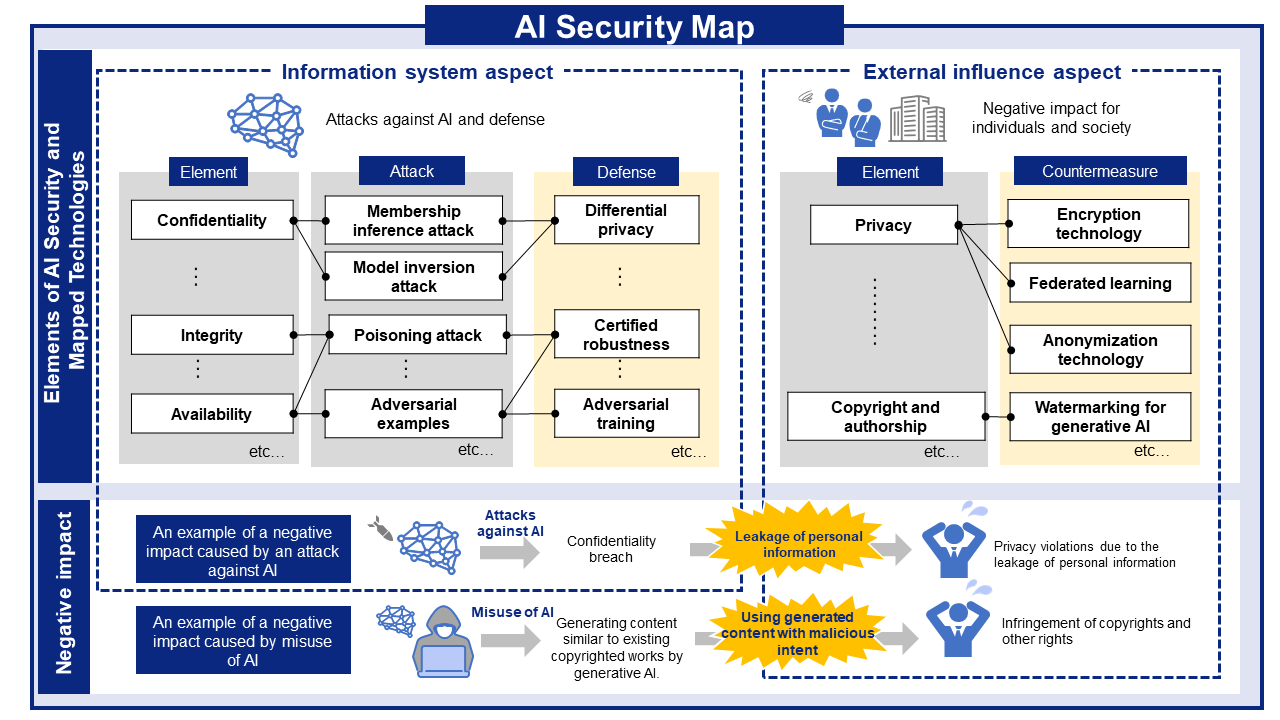
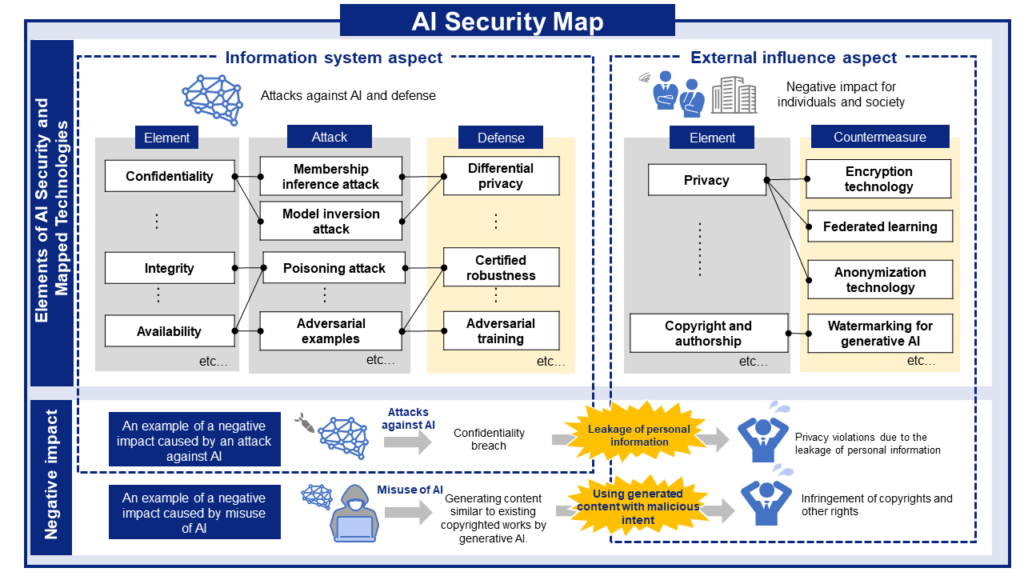
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
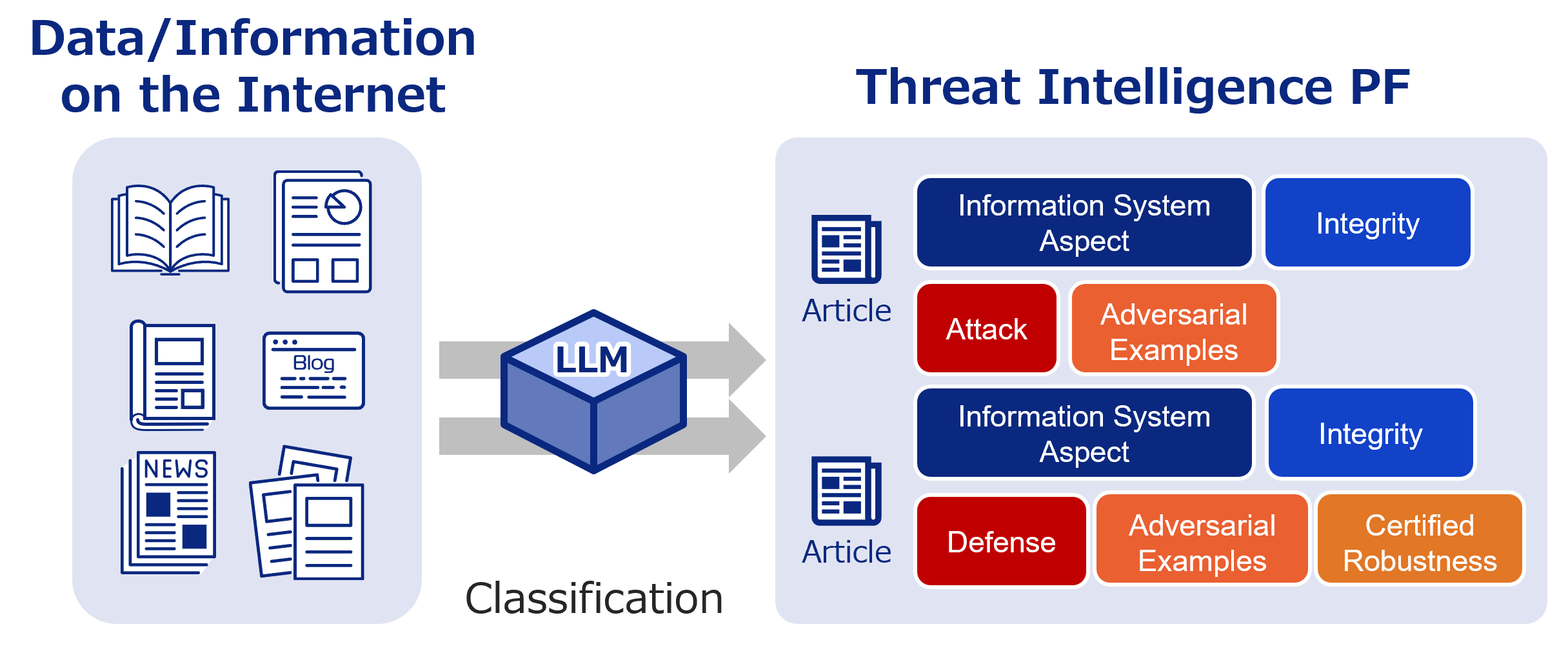
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

HoneyTrap: Deceiving Large Language Model Attackers to Honeypot Traps with Resilient Multi-Agent Defense
Authors: Siyuan Li, Xi Lin, Jun Wu, Zehao Liu, Haoyu Li, Tianjie Ju, Xiang Chen, Jianhua Li | Published: 2026-01-07
2026.01.072026.01.09

SoK: Privacy Risks and Mitigations in Retrieval-Augmented Generation Systems
Authors: Andreea-Elena Bodea, Stephen Meisenbacher, Alexandra Klymenko, Florian Matthes | Published: 2026-01-07
2026.01.072026.01.09

Jailbreaking LLMs & VLMs: Mechanisms, Evaluation, and Unified Defense
Authors: Zejian Chen, Chaozhuo Li, Chao Li, Xi Zhang, Litian Zhang, Yiming He | Published: 2026-01-07
2026.01.072026.01.09

-scaled.png)