Site Contents
Related News
Last updated: 2026-02-08 06:00
-
AIUC-1 operationalizes Cisco's AI Security Framework
2026-02-06 20:30 blogs.cisco.com -
Industry Analyst Jeff Kagan comments on AI Security Platform DeepKeep - EIN Presswire
2026-02-06 19:39 www.einpresswire.com -
Security Leaders Ramp Up Agentic Use Cases – While Protecting Against Shadow AI
2026-02-06 19:29 cloudwars.com -
Product security RegTech Nullify secures $12.5m seed funding - FinTech Global
2026-02-06 19:21 fintech.global -
Measuring ROI from AI Investments in Cybersecurity Programs: A Framework for Security Leaders
2026-02-06 18:15 hackread.com -
Shadow AI is the new Shadow IT, and most security teams are flying blind | SC Media
2026-02-06 18:09 www.scworld.com -
Zscaler Acquires SquareX to Advance Zero Trust Browser Security for the AI Era
2026-02-06 16:58 finance.yahoo.com -
Microsoft Cloud and AI Security Engineer Blueprint Survey Opportunity
2026-02-06 16:51 techcommunity.microsoft.com -
Okta: From Human Access To Increasingly Competitive Agentic AI Security Market
2026-02-06 16:17 seekingalpha.com -
Live Webinar | When AI Moves Faster Than Security: Enabling a Cyber-Resilient AI-Native Enterprise
2026-02-06 16:14 www.bankinfosecurity.com -
Psychology, AI and the Modern Security Program: A CISO's Guide - Infosecurity Magazine
2026-02-06 16:10 www.infosecurity-magazine.com -
Moltbook: Cutting Through the AI Hype to the Real Security Risks
2026-02-06 15:50 www.itsecurityguru.org -
Wiz + Spotify Backstage: Security at the Developer's Desk | Wiz Blog
2026-02-06 14:49 www.wiz.io -
Security concerns and skepticism are bursting the bubble of Moltbook, the viral AI social forum
2026-02-06 14:47 www.kare11.com -
How SCSU Is Rebuilding Campus Technology for the AI Era - BankInfoSecurity
2026-02-05 19:31 www.bankinfosecurity.com -
The security implementation gap: Why Microsoft is supporting Operation Winter SHIELD
2026-02-05 18:09 www.microsoft.com -
Cyberhaven Introduces Unified AI and Data Security Platform
2026-02-05 18:02 www.dbta.com -
n8n security woes roll on as new critical flaws bypass December fix - The Register
2026-02-05 17:41 www.theregister.com -
Q&A: Moltbook, OpenClaw, and the security risks of the new agentic-AI era | BetaKit
2026-02-05 17:26 betakit.com -
Salt Security warns autonomous AI agents are the next major security blind spot
2026-02-05 17:06 www.itsecurityguru.org
* This information has been collected using Google Alerts based on keywords set by our website. These data are obtained from third-party websites and content, and we do not have any involvement with or responsibility for their content.
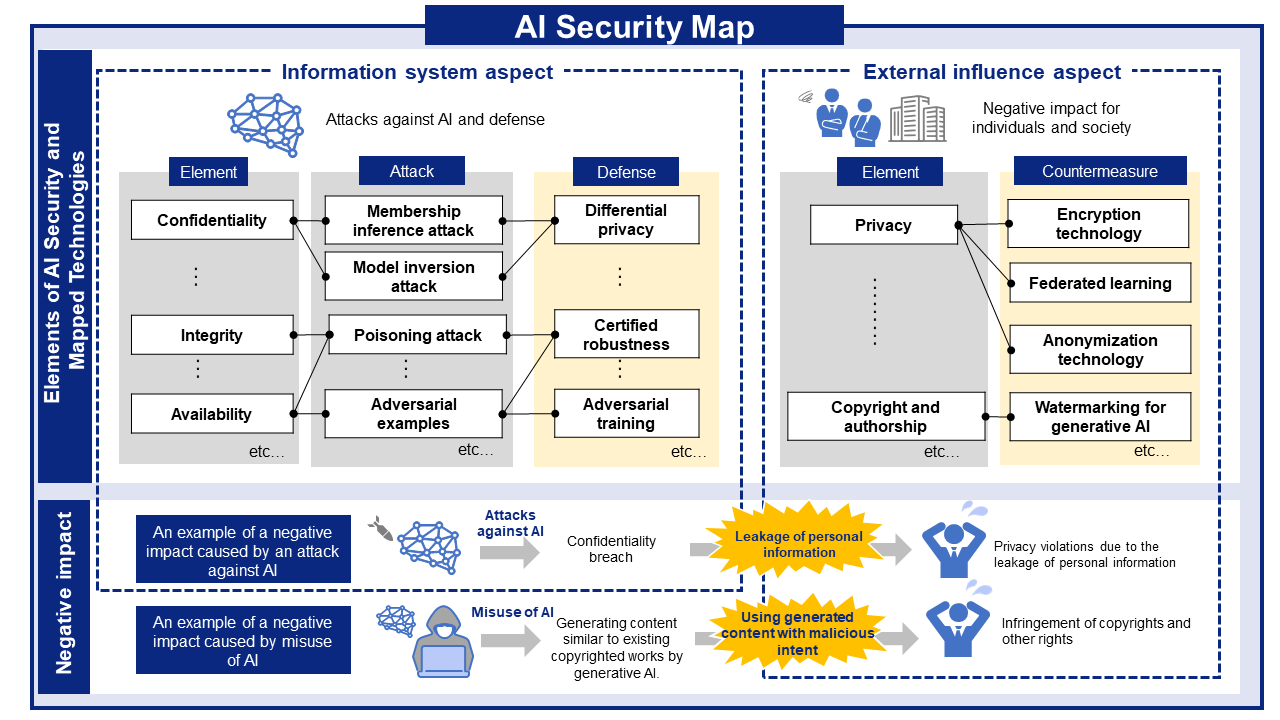
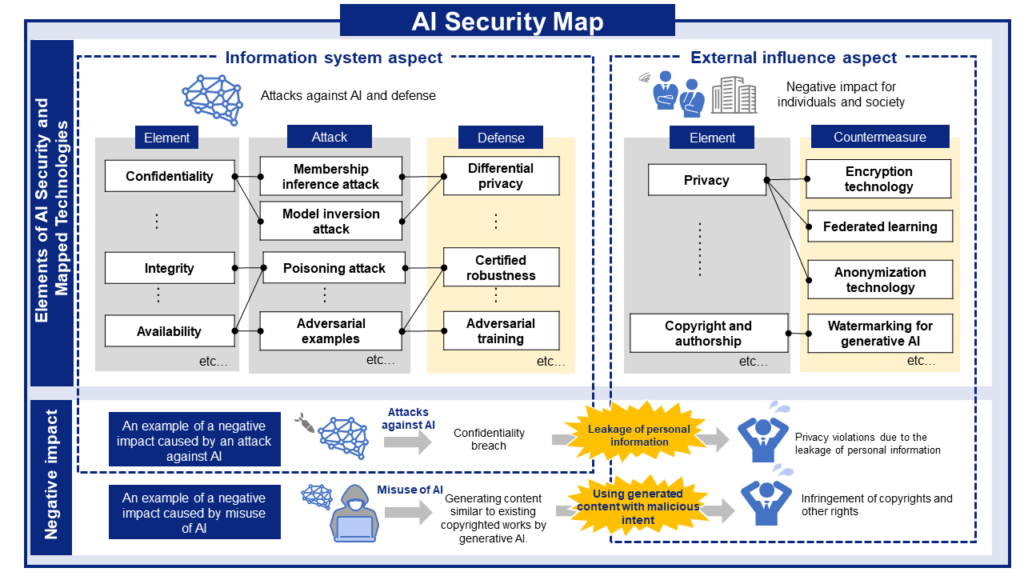
AI Risks, Impacts, and Mitigations at a Glance
AI security threats and related mitigations, organized from two perspectives: information Systems and People and Society.
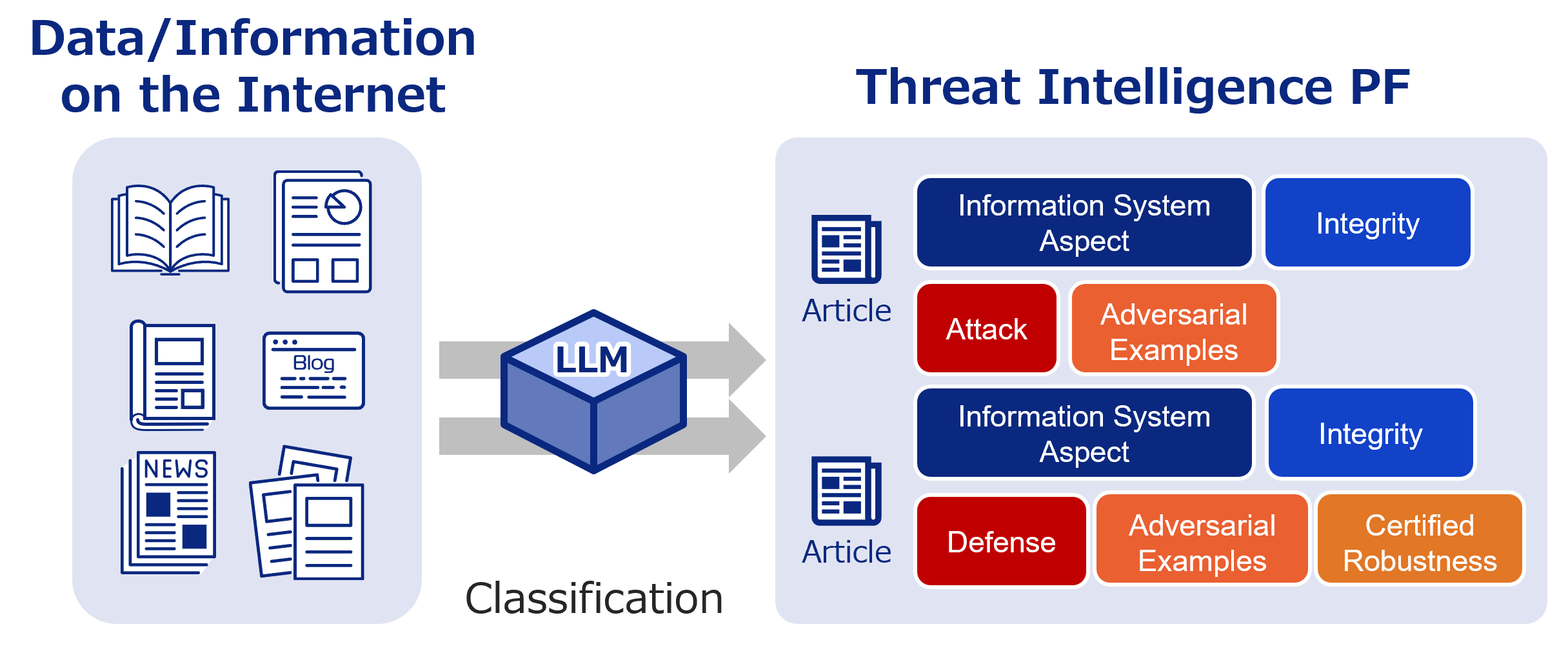
AI Security Information Gathering and Research
Labeled bibliographic information. Use it to research the latest trends and more.
Recent literature

Deep Learning for Contextualized NetFlow-Based Network Intrusion Detection: Methods, Data, Evaluation and Deployment
Authors: Abdelkader El Mahdaouy, Issam Ait Yahia, Soufiane Oualil, Ismail Berrada | Published: 2026-02-05
2026.02.052026.02.07

Clouding the Mirror: Stealthy Prompt Injection Attacks Targeting LLM-based Phishing Detection
Authors: Takashi Koide, Hiroki Nakano, Daiki Chiba | Published: 2026-02-05
2026.02.052026.02.07

BadTemplate: A Training-Free Backdoor Attack via Chat Template Against Large Language Models
Authors: Zihan Wang, Hongwei Li, Rui Zhang, Wenbo Jiang, Guowen Xu | Published: 2026-02-05
2026.02.052026.02.07

-scaled.png)