Overview
As AI technology evolves, research on AI security has become increasingly diverse and complex[1]. The scope of AI security research now extends beyond the three fundamental elements of information security—confidentiality, integrity, and availability (CIA)—to include factors related to trustworthiness, such as fairness and explainability. Existing knowledge frameworks have primarily organized these aspects from a technical perspective, lacking a systematic analysis of the interrelationships among these elements and the negative impacts on individuals and society resulting from compromise or misuse of AI. Therefore, we have examined these interconnections and impacts, and developed an AI Security Map that systematically organizes these relationships.
The AI Security Map encompasses AI, individuals, and society. It systematically organizes the elements and technologies related to AI security, while also considering the classification of attacks and defenses against AI, as well as the negative impacts on individuals and society resulting from AI being attacked or misused. By referring to the AI Security Map, one can understand the potential negative impacts on information systems if AI is compromised, along with the measures necessary to prevent such impacts. Additionally, the AI Security Map helps to clarify how these negative effects in AI-based systems relate to and influence individuals and society, and what kinds of adverse consequences may arise. Figure 1 provides an overview of the AI security map.
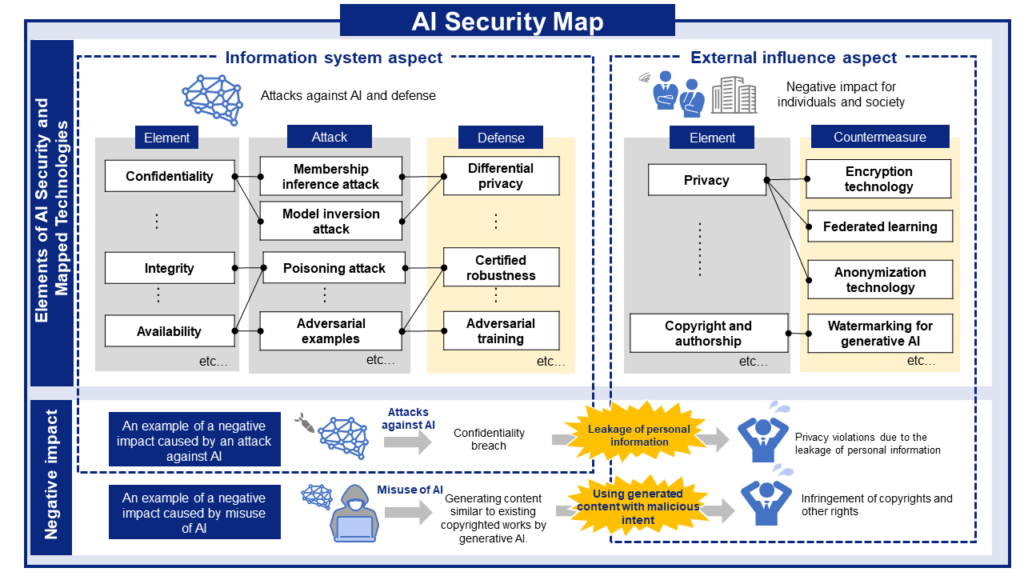
Figure 1 Overview of the AI Security Map.
Components of AI Security Map
The elements of the AI Security Map are categorized into two groups: the information system aspect and the external influence aspect.
Information system aspect
In this aspect, the elements that AI must satisfy within information systems are classified. The primary focus is on the three elements of information security, known as CIA (Confidentiality, Integrity, and Availability). Other elements are organized based on their being affected by the degradation of CIA. By examining the negative impacts on these elements, one can better understand their underlying causes and potential countermeasures. Additionally, it is assumed that the negative impacts on the elements classified under this category may influence external factors.
External influence aspect
In this aspect, elements that impact individuals and society, such as privacy violations and infringements of rights like copyright, are classified. The negative impacts in this aspect are assumed to arise not only from attacks on information systems that damage these elements but also from the misuse of AI. By examining the negative impacts on the elements within this aspect, one can understand which aspects of the information system are compromised and how such damage can affect people and society, as well as potential countermeasures.
Security targets
Table 1 shows the security targets defined in the AI Security Map. These security targets are subjects that could be affected by AI attacks or misuse. We assume four types of security targets.
Table 1 Security targets in AI security map
| Security target | Definition |
| AI system provider | An individual or organization that provides an information system using AI (AI system). |
| Consumer | An individual or organization that utilizes AI or AI systems. |
| Non-consumer | An individuals or organization that are not classified as consumers. |
| Society | A group composed of multiple people and organizations. |
Relationship of elements in AI Security Map
The AI security map organizes the relationships between the elements of the information system aspect and the external influence aspect. Specifically, damage or misuse of any element within the information system aspect is related to elements of the external influence aspect. Figure 2 shows an overview of the elements within the AI Security Map. Elements related to trustworthiness in the information system aspect are affected by breaches of the CIA. Conversely, elements of the external influence aspect are impacted by damage to elements within the information system aspect. Additionally, even when the elements of the information system aspect are properly maintained, the external influence aspect can still be affected due to the misuse of certain elements. By referring to the AI Security Map, one can understand these relationships.
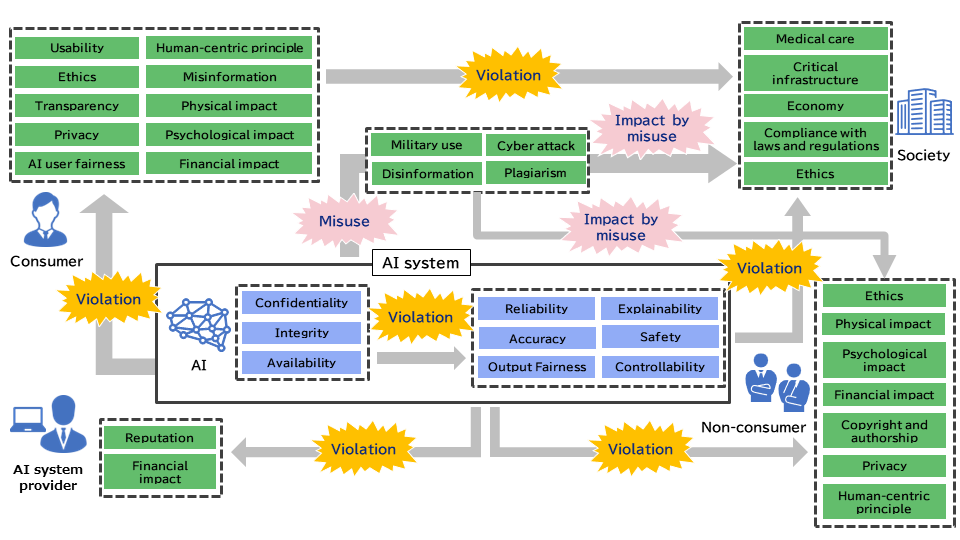
Figure 2. Relationships among elements in AI Security Map (blue indicates elements of the information system aspect, and green indicates elements of the external influence aspect).
Features of AI Security Map
The AI security map differs from existing survey papers [1][2] and guidelines in the following ways:
- It systematically considers and organizes not only the information system aspect, which is composed of elements that AI should satisfy, but also the external influence aspect, which consists of elements impacting individuals and society.
- It organizes the interrelationships among elements within the information system aspect.
- It organizes the interrelationships among elements within the external influence aspect.
- It considers the mutual relationships between the information system aspect and the external influence aspect, clarifying the relationship between AI security and individuals and society.
These features have not been addressed in previous frameworks and are expected to become increasingly important as AI is more widely utilized in society. We will continuously investigate the latest AI security trends, and we will periodically update the AI Security Map based on the results of these analyses.
Reference
[1] Chen, Huaming, and M. Ali Babar. “Security for machine learning-based software systems: A survey of threats, practices, and challenges.” ACM Computing Surveys 56.6 (2024): 1-38.
[2] Weidinger, Laura, et al. “Taxonomy of risks posed by language models.” Proceedings of the 2022 ACM conference on fairness, accountability, and transparency. 2022.

-scaled.png)
